of 8 pipes.
Explicitly Excluding Traffic from Shaping
If no pipe is specified in a pipe rule list then traffic that triggers the rule will not flow through any
pipe. It also means that the triggering traffic will not be subject to any other matching pipe rules that
might be found later in the rule set.
This provides a means to explicitly exclude particular traffic from traffic shaping. Such rules are not
absolutely necessary but if placed at the beginning of the pipe rule set, they can guard against
accidental traffic shaping by later rules.
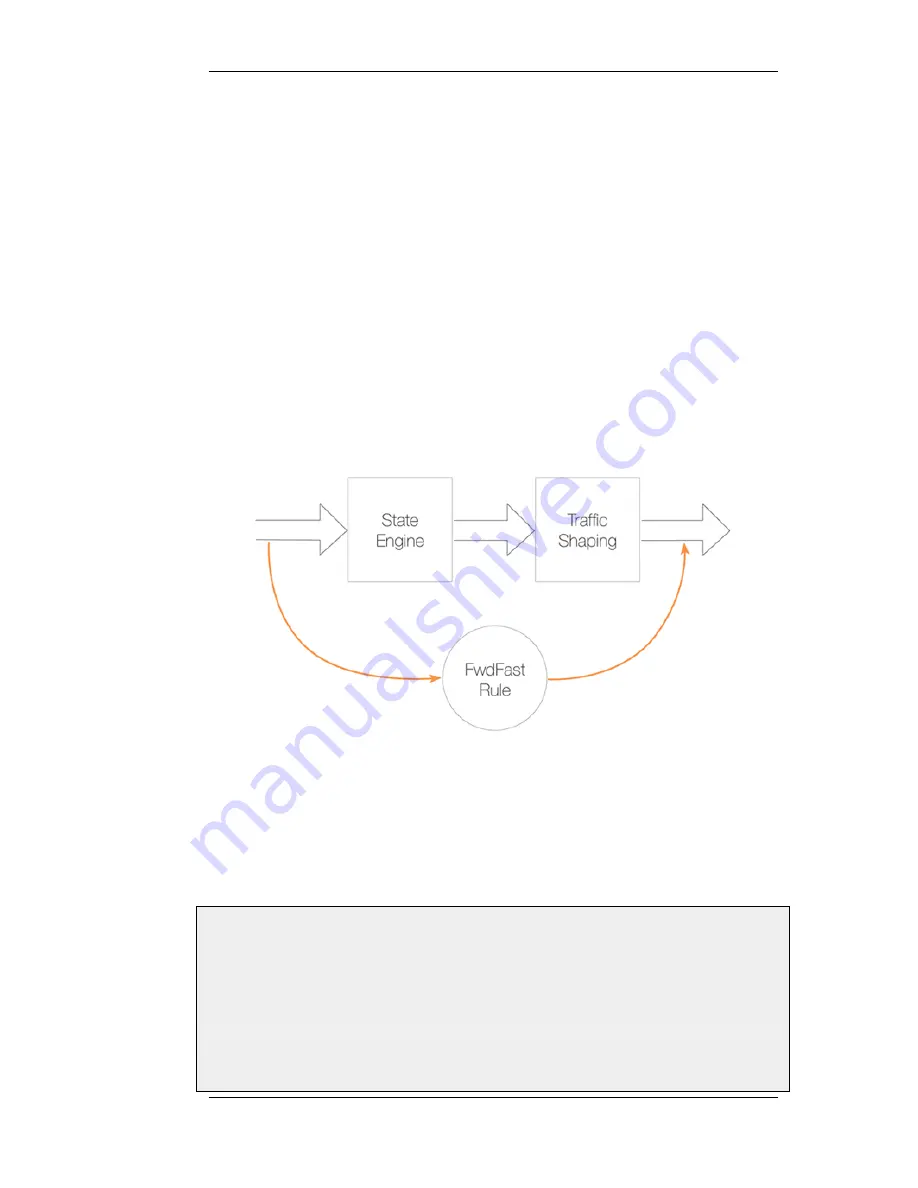
Pipes Will Not Work With FwdFast IP Rules
It is important to understand that traffic shaping will not work with traffic that is flows as a result of
triggering a FwdFast IP rule in the NetDefendOS IP rule sets.
The reason for this is that traffic shaping is implemented by using the NetDefendOS state engine
which is the subsystem that deals with the tracking of connections. FwdFast IP rules do not set up a
connection in the state engine. Instead, packets are considered not to be part of a connection and are
forwarded individually to their destination, bypassing the state engine.
Figure 10.2. FwdFast Rules Bypass Traffic Shaping
10.1.3. Simple Bandwidth Limiting
The simplest use of pipes is for bandwidth limiting. This is also a scenario that does not require
much planning. The example that follows applies a bandwidth limit to inbound traffic only. This is
the direction most likely to cause problems for Internet connections.
Example 10.1. Applying a Simple Bandwidth Limit
Begin with creating a simple pipe that limits all traffic that gets passed through it to 2 megabits per second,
regardless of what traffic it is.
Command-Line Interface
gw-world:/> add Pipe std-in LimitKbpsTotal=2000
10.1.3. Simple Bandwidth Limiting
Chapter 10. Traffic Management
454
Summary of Contents for DFL-1600 - Security Appliance
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27 ...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79 ...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146 ...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227 ...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241 ...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339 ...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360 ...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382 ...
Page 386: ... The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386 ...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439 ...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450 ...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488 ...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503 ...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510 ...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533 ...






































