The consequence of a full table can be that stickiness will be lost for any discarded source IP
addresses. The administrator should therefore try to ensure that the Max Slots parameter is set to
a value that can accommodate the expected number of connections that require stickiness.
The default value for this setting is 2048 slots in the table.
•
Net Size
The processing and memory resources required to match individual IP addresses when
implementing stickiness can be significant. By selecting the Network Stickiness option these
resource demands can be reduced.
When the Network Stickiness option is selected, the Net Size parameter specifies the size of the
network which should be associated with the source IP of new connections. A stickiness table
lookup does not then compare individual IP addresses but instead compares if the source IP
address belongs to the same network as a previous connection already in the table. If they belong
to the same network then stickiness to the same server will result.
The default value for this setting is a network size of 24.
10.4.4. SLB Algorithms and Stickiness
This section discusses further how stickiness functions with the different SLB algorithms.
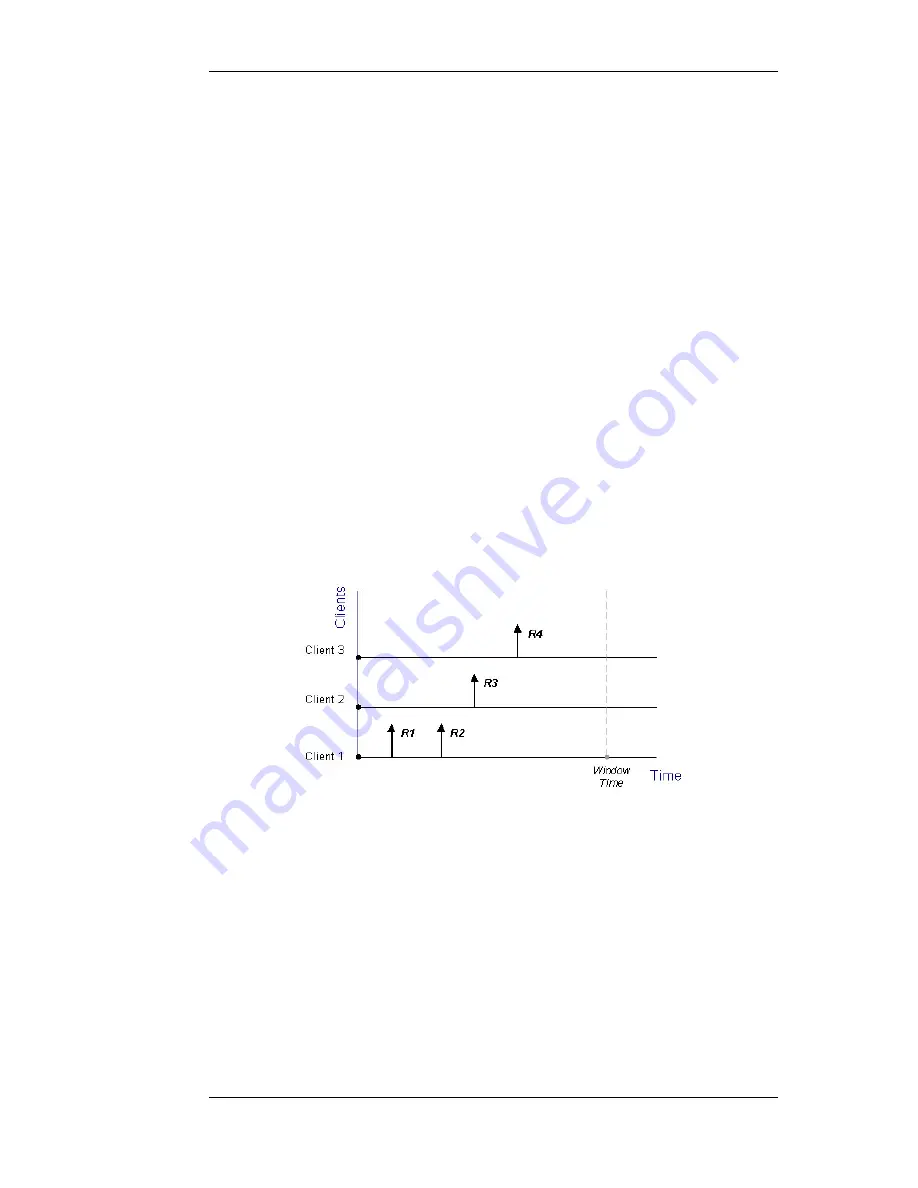
An example scenario is illustrated in the figure below. In this example, the NetDefend Firewall is
responsible for balancing connections from 3 clients with different addresses to 2 servers. Stickiness
is enabled.
Figure 10.10. Connections from Three Clients
When the round-robin algorithm is used, the first arriving requests R1 and R2 from Client 1 are both
assigned to one sever, say Server 1, according to stickiness. The next request R3 from Client 2 is
then routed to Server 2. When R4 from Client 3 arrives, Server 1 gets back its turn again and will be
assigned with R4.
10.4.4. SLB Algorithms and Stickiness
Chapter 10. Traffic Management
483
Summary of Contents for DFL-1600 - Security Appliance
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27 ...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79 ...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146 ...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227 ...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241 ...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339 ...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360 ...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382 ...
Page 386: ... The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386 ...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439 ...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450 ...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488 ...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503 ...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510 ...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533 ...









































