63
CHAPTER 4: USER AUTHENTICATION
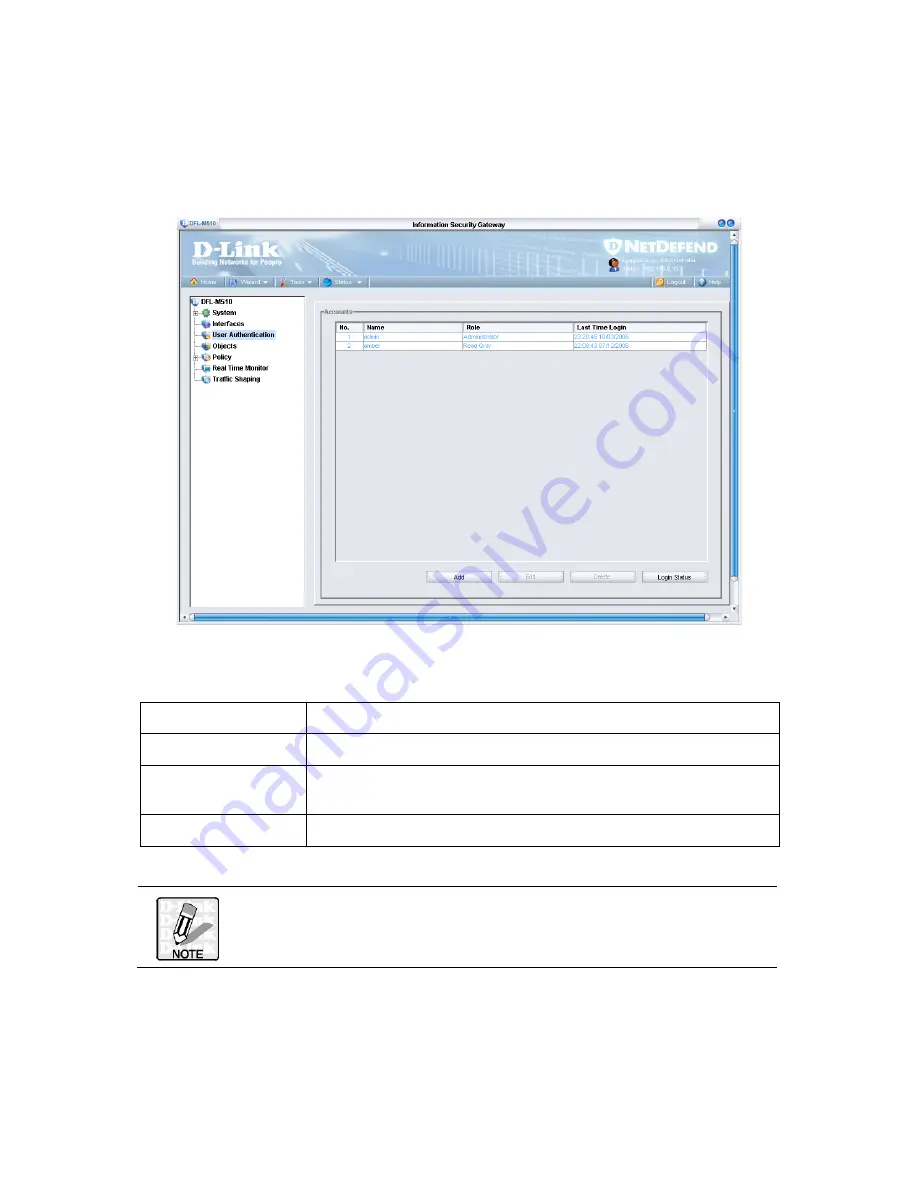
THE USER AUTHENTICATION SCREEN
After you log on, click
User Authentication
to open the following screen.
ACCOUNTS
No.
Shows the current number of accounts
Name
Shows the name for each account
Role
Shows the shows the level of the user
’
s policy:
Administrator; Read Only;
or
Write.
Last Time Login
Shows the last time the account was accessed
Only users that are assigned the Administrator role can edit the
Account and Hosts/Groups menus.
Summary of Contents for DFL-M510
Page 2: ......
Page 6: ...iv ...
Page 60: ...51 When the settings are processed the following screen appears 5 Click OK to finish ...
Page 80: ...71 3 Enter a file name and click Save 4 Click OK to confirm the export 5 Click OK to continue ...
Page 95: ...86 5 Under Group Host select PM and click Apply ...
















































