DGS-1510 Series Gigabit Ethernet SmartPro Switch Web UI Reference Guide
143
To view the following window, click
L3 Features > IPv4 Static/Default Route
, as shown below:
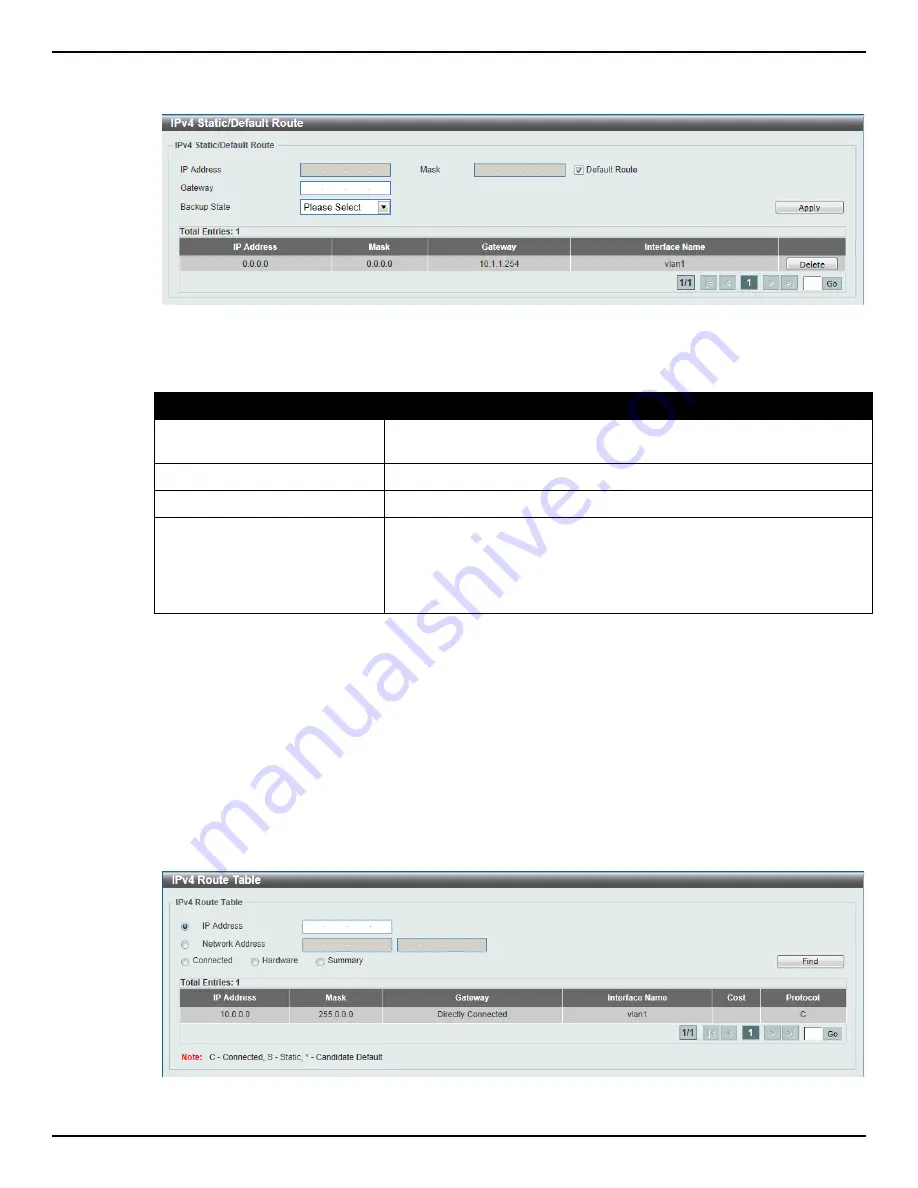
Figure 6-9 IPv4 Static/Default Route window
The fields that can be configured are described below:
Parameter
Description
IP Address
Enter the IPv4 address for this route here. Tick the
Default Route
check box to use the default route as the IPv4 address.
Mask
Enter the IPv4 network mask for this route here.
Gateway
Enter the gateway address for this route here.
Backup State
Select the backup state option here. Options to choose from are
Primary
, and
Backup
. When the
Primary
option is selected, the route
will be used as the primary route to the destination. When the
Backup
option is selected, the route will be used as the backup route to the
destination.
Click the
Apply
button to accept the changes made.
Click the
Delete
button to remove the specific entry.
Enter a page number and click the
Go
button to navigate to a specific page when multiple pages exist.
IPv4 Route Table
This window is used to view and configure the IPv4 route table settings.
To view the following window, click
L3 Features > IPv4 Route Table
, as shown below:
Figure 6-10 IPv4 Route Table window
Summary of Contents for DGS-1510 Series
Page 1: ...1...
















































