DGS-1510 Series Gigabit Ethernet SmartPro Switch Web UI Reference Guide
337
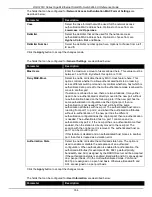
Figure 9-76 Network Access Authentication Sessions Information window
The fields that can be configured are described below:
Parameter
Description
Port
Select the appropriate switch unit and port used for the query here.
MAC Address
Enter the MAC address used here.
Protocol
Select the protocol option used here. Options to choose from are
MAC
,
WAC
,
JWAC
, and
DOT1X
.
Click the
Apply
button to accept the changes made.
Click the
Clear by Port
button to the clear the information based on the port selected.
Click the
Clear by MAC
button to the clear the information based on the MAC address entered.
Click the
Clear by Protocol
button to the clear the information based on the protocol selected.
Click the
Clear All
button to clear all the information in this table.
Click the
Find
button to locate a specific entry based on the information entered.
Click the
View All
button to locate and display all the entries.
Safeguard Engine
Periodically, malicious hosts on the network will attack the Switch by utilizing packet flooding (ARP Storm)
or other methods. These attacks may increase the switch’s CPU load beyond its capability. To alleviate
this problem, the Safeguard Engine function was added to the Switch’s software.
The Safeguard Engine can help the overall operability of the Switch by minimizing the workload of the
Switch while the attack is ongoing, thus making it capable to forward essential packets over its network in
a limited bandwidth.
If the CPU load rises above the rising threshold value, the Safeguard Engine function will be activated
and the Switch will enter the exhausted mode. In the exhausted mode, the Switch will limit the bandwidth
available for ARP and broadcast IP packets. If the CPU load falls below the falling threshold value, the
Safeguard Engine will be deactivated and the Switch will exit the exhausted mode and enter the normal
mode.
Packets that are destined to the CPU can be classified into three groups. These groups, otherwise known
as sub-interfaces, are logical interfaces that the CPU will use to identify certain types of traffic. The three
groups are
Protocol
,
Manage
, and
Route
. Generally, the
Protocol
group should receive the highest
priority when the Switch’s CPU processes received packets and the
Route
group should receive the
lowest priority as the Switch’s CPU usually does get involved in the processing of routing packets. In the
Protocol
group, packets are protocol control packets identified by the router. In the
Manage
group,
Summary of Contents for DGS-1510 Series
Page 1: ...1...