DIS-200G Series Industrial Gigabit Ethernet Smart Managed Switch
44
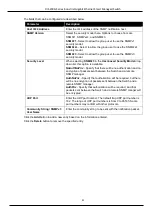
Click the
Back
button to return to the previous window.
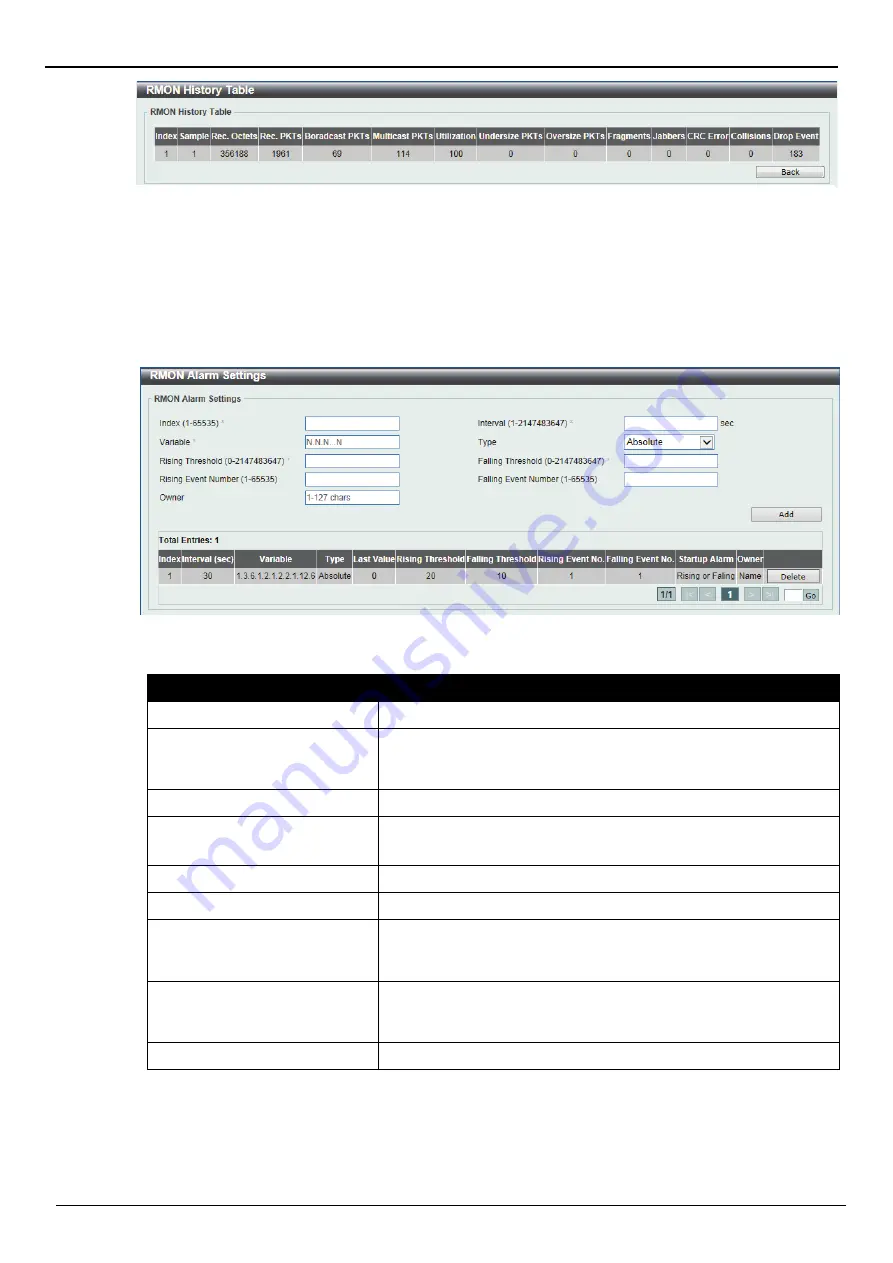
RMON Alarm Settings
This window is used to configure and display alarm entries to monitor an interface.
To view the following window, click
Management > RMON > RMON Alarm Settings
, as shown below:
The fields that can be configured are described below:
Parameter
Description
Index
Enter the alarm index. The range is from 1 to 65535.
Interval
Enter the interval in seconds for the sampling of the variable and
checking against the threshold. The valid range is from 1 to
2147483647 seconds.
Variable
Enter the object identifier of the variable to be sampled.
Type
Select the monitoring type. Options to choose from are
Absolute
and
Delta
.
Rising Threshold
Enter the rising threshold value between 0 and 2147483647.
Falling Threshold
Enter the falling threshold value between 0 and 2147483647.
Rising Event Number
Enter the index of the event entry that is used to notify the rising
threshold crossing event. The valid range is from 1 to 65535. If not
specified, no action is taken while crossing the ringing threshold.
Falling Event Number
Enter the index of the event entry that is used to notify the falling
threshold crossing event. The valid range is from 1 to 65535. If not
specified, no action is taken while crossing the falling threshold.
Owner
Enter the owner string up to 127 characters.
Click the
Add
button to add a new entry based on the information entered.
Click the
Delete
button to remove the specified entry.
Enter a page number and click the
Go
button to navigate to a specific page when multiple pages exist.
Figure 5-14 RMON History Table window
Figure 5-15 RMON Alarm Settings window