49
Using the Configuration Utility (continued)
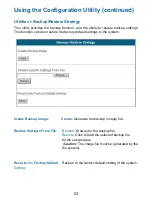
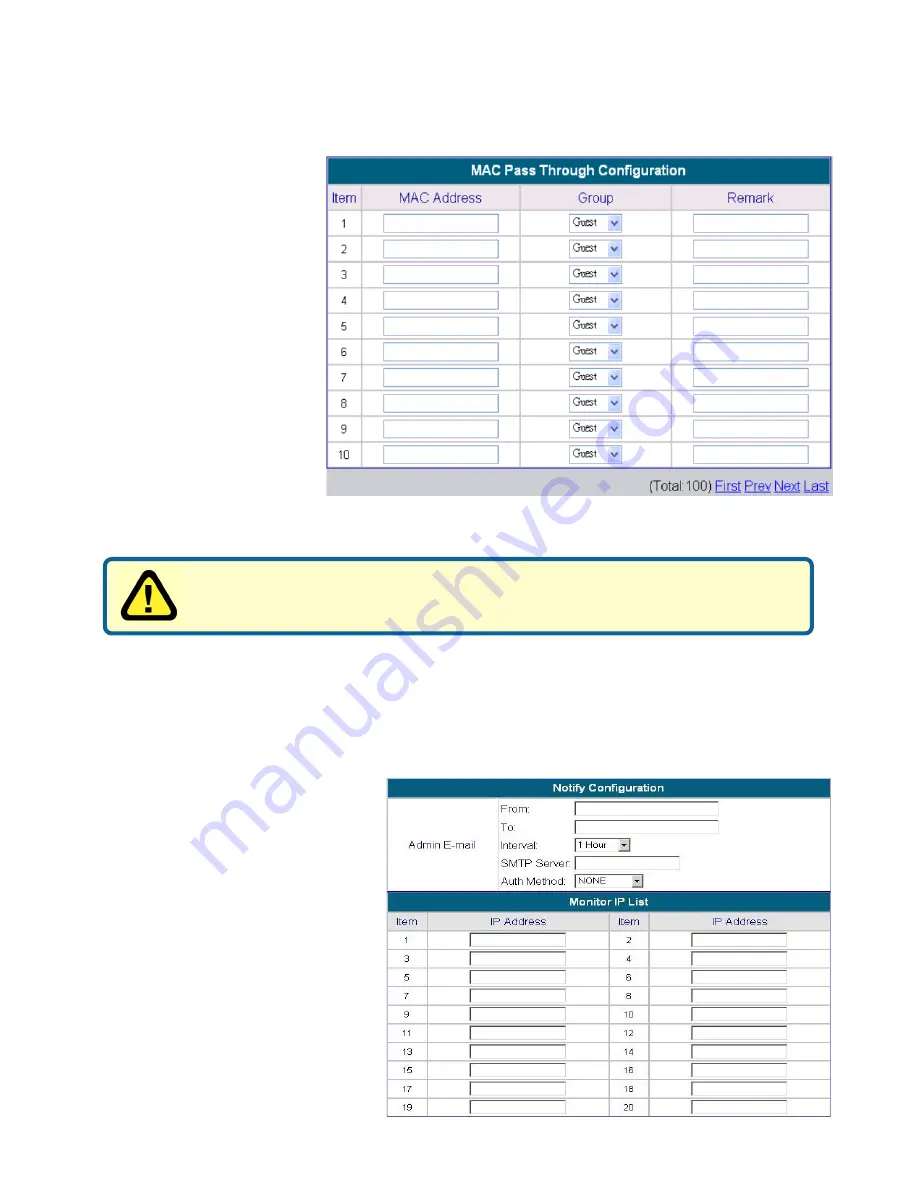
Network Configuration > MAC Pass Through Configuration
You can also bypass
authentication based on
the MAC address at the
user end. Please enter
the MAC address of the
user on this interface.
This system permits at
most 100 MAC
addresses to have
network access rights
without going through
authentication. The
format of the MAC
address is
XX:XX:XX:XX:XX:XX.
These settings will be effective immediately after you click Apply.
Warning: Permitting specific MAC addresses to have access rights
without going through authentication may cause security problems.
Network Configuration > Monitor IP List
The system will send out the packet regularly to monitor the connection
status of the IP addresses on the list. If the monitored IP address does
not respond, the system will
send an e-mail to the
administrator. After enter
the related information
and click Apply, these
settings will be effective
immediately. You can
click Monitor to check
the current status of all
the monitored IP. The
system provides 40 IP
addresses a most on the
"Monitor IP List" to set.