Unified Services Router
User Manual
142
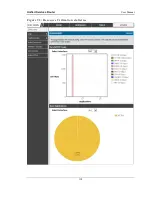
Fig ur e 96: A P spec ifi c statist ics
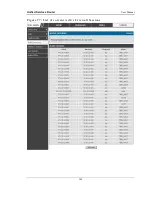
10.3 Active Connections
10.3.1 Sessions through the Router
Status > Active Sessions
This table lists the active internet sessions through the router‘s firewall. The
session‘s protocol, state, local and remote IP addresses are shown.
Summary of Contents for DSR-250N
Page 2: ...User Manual Unified Services Router D Link Corporation Copyright 2011 http www dlink com...
Page 7: ...Unified Services Router User Manual 5 Appendix F Product Statement 214...
Page 14: ......
Page 119: ...Unified Services Router User Manual 117 Figure 74 Advanced Switch Settings...
Page 138: ...Unified Services Router User Manual 136 Figure 90 Device Status display...
Page 140: ...Unified Services Router User Manual 138 Figure 92 Resource Utilization statistics...
Page 141: ...Unified Services Router User Manual 139 Figure 93 Resource Utilization data continued...
Page 145: ...Unified Services Router User Manual 143 Figure 97 List of current Active Firewall Sessions...
Page 154: ......
Page 158: ......