82 © 2001-2008 D-Link Corporation. All Rights Reserved.
D-Link Unified Access Point Administrator’s Guide
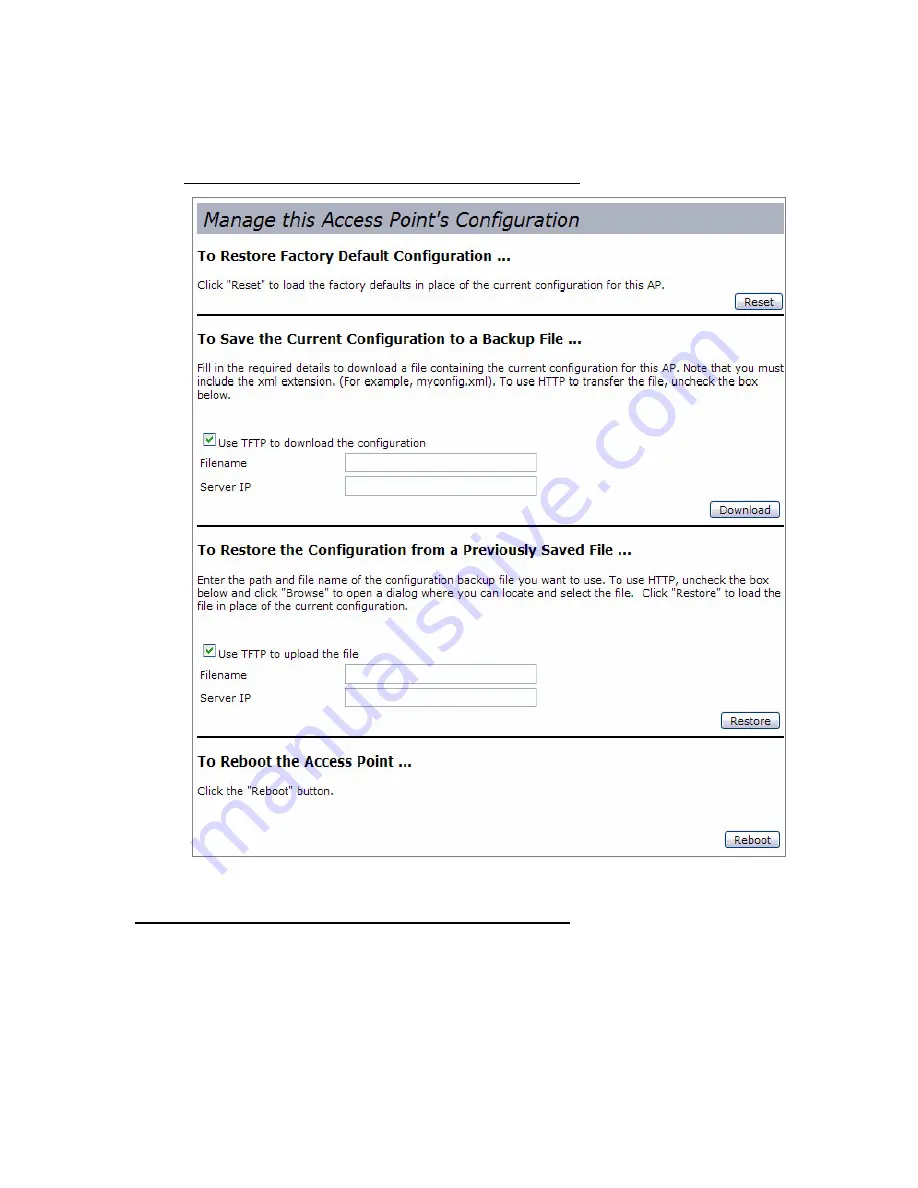
Click the Configuration tab to access the configuration management page, which
Figure 16
shows.
Figure 16. Configuration Management
The following sections describe the fields and options on the Configuration page.
Resetting the Factory Default Configuration
If you are experiencing problems with the Unified Access Point and have tried all other
troubleshooting measures, click Reset. This restores factory defaults and clears all settings,
including settings such as a new password or wireless settings. You can also use the reset
button on the back panel to reset the system to the default configuration. For information about
the reset button, see
“Using the Reset Button”
on page 23.
















































