•
Address to use as source IP - It is possible to specify a particular IP address as the source
interface IP for the GRE tunnel. The tunnel setup will appear to be initiated by this IP address
instead of the IP address of the interface that actually sets up the tunnel.
This might be done if, for example, if ARP publishing is being used and the tunnel is to be setup
using an ARP published IP address.
GRE and the IP Rule Set
An established GRE tunnel does not automatically mean that all traffic coming from or to that GRE
tunnel is trusted. On the contrary, network traffic coming from the GRE tunnel will be transferred to
the NetDefendOS IP rule set for evaluation. The source interface of the network traffic will be the
name of the associated GRE Tunnel.
The same is true for traffic in the opposite direction, that is, going into a GRE tunnel. Furthermore a
Route has to be defined so NetDefendOS knows what IP addresses should be accepted and sent
through the tunnel.
An Example GRE Scenario
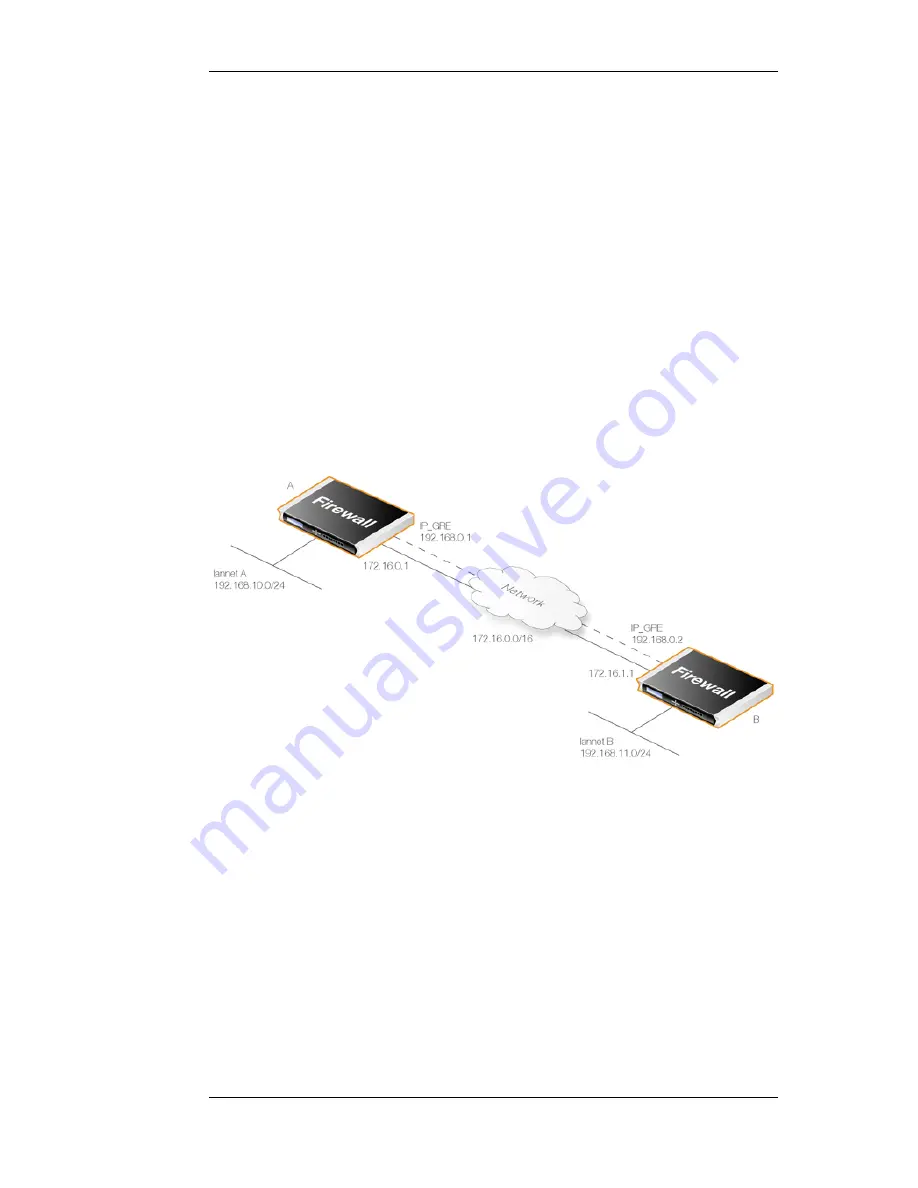
The diagram above shows a typical GRE scenario, where two NetDefend Firewalls A and B must
communicate with each other through the intervening internal network 172.16.0.0/16.
Any traffic passing between A and B is tunneled through the intervening network using a GRE
tunnel and since the network is internal and not public there is no need for encryption.
Setup for NetDefend Firewall "A"
Assuming that the network 192.168.10.0/24 is lannet on the lan interface, the steps for setting up
NetDefendOS on A are:
1.
In the address book set up the following IP objects:
•
remote_net_B: 192.168.11.0/24
•
remote_gw: 172.16.1.1
•
ip_GRE: 192.168.0.1
3.3.5. GRE Tunnels
Chapter 3. Fundamentals
109
Summary of Contents for NetDefend DFL-260E
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382...
Page 386: ...The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533...







































