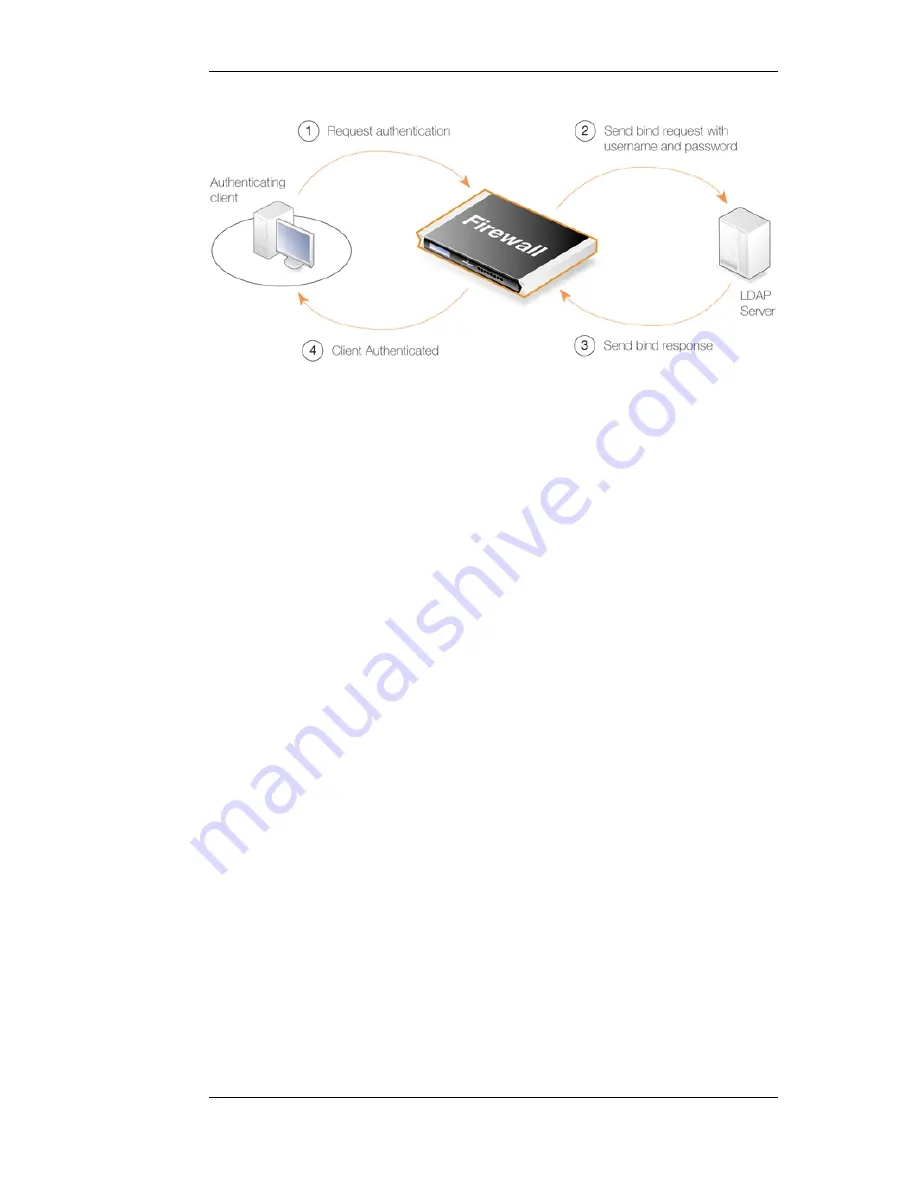
Figure 8.1. Normal LDAP Authentication
The processing is different if a group membership is being retrieved since a request is sent to the
LDAP server to search for memberships and any group memberships are then sent back in the
response.
B. PPP Authentication with CHAP, MS-CHAPv1 or MS-CHAPv2 Encryption
If PPP with CHAP, MS-CHAPv1 or MS-CHAPv2 is used for authentication, a digest of the user's
password will be sent to NetDefendOS by the client. NetDefendOS cannot just forward this digest
to the LDAP server since this won't be understood. The solution is for NetDefendOS to obtain the
password in plain-text from the LDAP server, create a digest itself, and then compare the created
digest with the digest from the client. If the two are the same, authentication is successful but it is
NetDefendOS that makes the authentication decision and not the LDAP server.
To retrieve the password from the LDAP server, two things are needed:
•
The Password Attribute parameter needs to be specified when defining the server to
NetDefendOS. This will be the ID of the field on the LDAP server that will contain the
password when it is sent back.
This ID must be different from the default password attribute (which is usually userPassword
for most LDAP servers). A suggestion is to use the description field in the LDAP database.
•
In order for the server to return the password in the database field with the ID specified, the
LDAP administrator must make sure that the plain text password is found there. LDAP servers
store passwords in encrypted digest form and do not provide automatic mechanisms for doing
this. It must therefore be done manually by the administrator as they add new users and change
existing users passwords.
This clearly involves some effort from the administrator, as well as leaving passwords
dangerously exposed in plain text form on the LDAP server. These are some of the reasons why
LDAP may not be viewed as a viable authentication solution for CHAP, MS-CHAPv1 or
MS-CHAPv2 encrypted PPP.
When NetDefendOS receives the password digest from the client, it initiates a Search Request to the
LDAP server. The server replies with a Search Response which will contains the user's password
and any group memberships. NetDefendOS is then able to compare digests. The diagram below
illustrates this process.
8.2.4. External LDAP Servers
Chapter 8. User Authentication
371
Summary of Contents for NetDefend DFL-260E
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382...
Page 386: ...The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533...










































