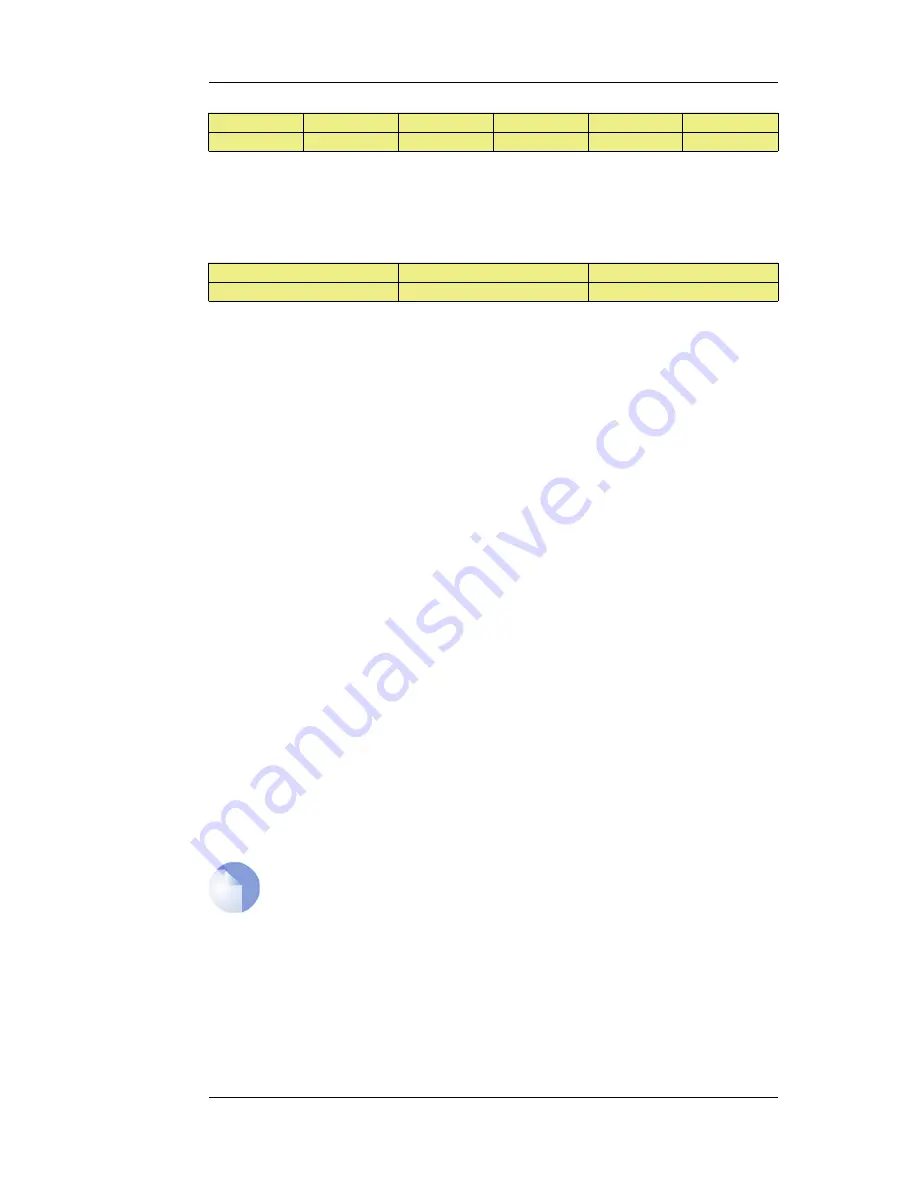
Action
Src Interface
Src Network
Dest Interface
Dest Network
Service
Allow
ipsec_tunnel
remote_net
lan
lannet
All
The Service used in these rules is All but it could be a predefined service.
6.
Define a new NetDefendOS Route which specifies that the VPN Tunnel ipsec_tunnel is the
Interface to use for routing packets bound for the remote network at the other end of the tunnel.
Interface
Network
Gateway
ipsec_tunnel
remote_net
<empty>
9.2.2. IPsec LAN to LAN with Certificates
LAN to LAN security is usually provided with pre-shared keys but sometimes it may be desirable to
use X.509 certificates instead. If this is the case, Certificate Authority (CA) signed certificates may
be used and these come from an internal CA server or from a commercial supplier of certificates.
Creating a LAN to LAN tunnel with certificates follows exactly the same procedures as the previous
section where a pre-shared key was used. The difference is that certificates now replace pre-shared
keys for authentication.
Two unique sets of two CA signed certificates (two for either end, a root certificate and a gateway
certificate) are required for a LAN to LAN tunnel authentication.
The setup steps are as follows:
1.
Open the WebUI management interface for the NetDefend Firewall at one end of the tunnel.
2.
Under Authentication Objects, add the Root Certificate and Host Certificate into
NetDefendOS. The root certificate needs to have 2 parts added: a certificate file and a private
key file. The gateway certificate needs just the certificate file added.
3.
Set up the IPsec Tunnel object as for pre-shared keys, but specify the certificates to use under
Authentication. Do this with the following steps:
a.
Enable the X.509 Certificate option.
b.
Add the Root Certificate to use.
c.
Select the Gateway Certificate.
4.
Open the WebUI management interface for the NetDefend Firewall at the other side of the
tunnel and repeat the above steps with a different set of certificates.
Note: The system time and date should be correct
The NetDefendOS date and time should be set correctly since certificates have an
expiry date and time.
Also review Section 9.6, “CA Server Access” below, which describes important considerations for
certificate validation.
Self-signed certificates instead of CA signed can be used for LAN to LAN tunnels but the Web
Interface and other interfaces do not have a feature to generate them. Instead, they must be
generated by another utility and imported into NetDefendOS. This means that they are not truly
self-signed since they are generated outside of NetDefendOS control and it should be remembered
that there is no guarantee that their private key is unique. However, the security provided can still be
9.2.2. IPsec LAN to LAN with
Certificates
Chapter 9. VPN
389
Summary of Contents for NetDefend DFL-260E
Page 27: ...1 3 NetDefendOS State Engine Packet Flow Chapter 1 NetDefendOS Overview 27...
Page 79: ...2 7 3 Restore to Factory Defaults Chapter 2 Management and Maintenance 79...
Page 146: ...3 9 DNS Chapter 3 Fundamentals 146...
Page 227: ...4 7 5 Advanced Settings for Transparent Mode Chapter 4 Routing 227...
Page 241: ...5 4 IP Pools Chapter 5 DHCP Services 241...
Page 339: ...6 7 Blacklisting Hosts and Networks Chapter 6 Security Mechanisms 339...
Page 360: ...7 4 7 SAT and FwdFast Rules Chapter 7 Address Translation 360...
Page 382: ...8 3 Customizing HTML Pages Chapter 8 User Authentication 382...
Page 386: ...The TLS ALG 9 1 5 The TLS Alternative for VPN Chapter 9 VPN 386...
Page 439: ...Figure 9 3 PPTP Client Usage 9 5 4 PPTP L2TP Clients Chapter 9 VPN 439...
Page 450: ...9 7 6 Specific Symptoms Chapter 9 VPN 450...
Page 488: ...10 4 6 Setting Up SLB_SAT Rules Chapter 10 Traffic Management 488...
Page 503: ...11 6 HA Advanced Settings Chapter 11 High Availability 503...
Page 510: ...12 3 5 Limitations Chapter 12 ZoneDefense 510...
Page 533: ...13 9 Miscellaneous Settings Chapter 13 Advanced Settings 533...









































