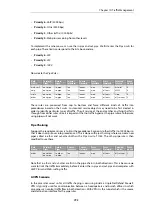
In the illustration below the minimum precedence is 2 and the maximum precedence is 6.
Precedence 2 is taken as the best effort precedence.
Figure 10.5. Minimum and Maximum Pipe Precedence
Lowest Precedence Limits
It is usually not needed to have a limit specified for the lowest (best effort) precedence since this
precedence simply uses any spare bandwidth not used by higher precedences. However, a limit
could be specified if there is a need to restrict the bandwidth used by the lowest precedence.
This might be the case if a particular traffic type always gets the lowest precedence but needs to
have restricted bandwidth usage.
Precedences Only Apply When a Pipe is Full
Precedences have no effect until the total limit specified for a pipe is reached. This is true
because until the pipe limit is reached (it becomes "full") there is no competition between
precedences.
When the pipe is full, traffic is prioritized by NetDefendOS according to precedence with higher
precedence packets that do not exceed the precedence limit being sent before lower
precedence packets. Lower precedence packets are buffered until they can be sent. If buffer
space becomes exhausted then they are dropped.
If a total limit for a pipe is not specified, it is the same as saying that the pipe has unlimited
bandwidth and consequently it can never become full so precedences have no meaning.
Applying Precedences
Continuing to use the previous traffic shaping example, let us add the requirement that SSH and
Telnet traffic is to have a higher priority than all other traffic. To do this we add a Pipe Rule
specifically for SSH and Telnet and set the priority in the rule to be a higher priority, say 2. We
specify the same pipes in this new rule as are used for other traffic.
The effect of doing this is that the SSH and Telnet rule sets the higher priority on packets related
to these services and these packets are sent through the same pipe as other traffic. The pipe then
makes sure that these higher priority packets are sent first when the total bandwidth limit
Chapter 10: Traffic Management
786
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...