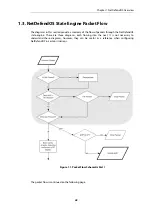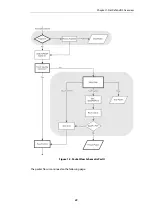
1.2. NetDefendOS Architecture
This section looks at the overall architecture of the NetDefendOS software product and describes
some of the key concepts that lie behind its design.
1.2.1. State-based Architecture
The NetDefendOS architecture is centered around the concept of state-based connections.
Traditional IP routers or switches commonly inspect all packets and then perform forwarding
decisions based on information found in the packet headers. With this approach, packets are
forwarded without any sense of context which eliminates any possibility to detect and analyze
complex protocols and enforce corresponding security policies.
Stateful Inspection
NetDefendOS employs a technique called
stateful inspection
which means that it inspects and
forwards traffic on a per-connection basis. NetDefendOS detects when a new connection is
being established, and keeps a small piece of information or
state
in its
state table
for the lifetime
of that connection. By doing this, NetDefendOS is able to understand the context of the network
traffic which enables it to perform in-depth traffic scanning, apply bandwidth management and
a variety of other functions.
The stateful inspection approach additionally provides high throughput performance with the
added advantage of a design that is highly scalable. The NetDefendOS subsystem that
implements stateful inspection will sometimes be referred to in documentation as the
NetDefendOS
state-engine
.
1.2.2. NetDefendOS Building Blocks
The basic building blocks in NetDefendOS are interfaces, logical objects and various types of
rules (or rule sets).
Interfaces
Interfaces
are the doorways through which network traffic enters or leaves the NetDefend
Firewall. Without interfaces, a NetDefendOS system has no means for receiving or sending traffic.
The following types of interface are supported in NetDefendOS:
•
Physical interfaces - These correspond to the actual physical Ethernet interfaces.
•
Sub-interfaces - These include VLAN and PPPoE interfaces.
•
Tunnel interfaces - Used for receiving and sending traffic through VPN tunnels.
Interface Symmetry
The NetDefendOS interface design is symmetric, meaning that the interfaces of the device are
not fixed as being on the "insecure outside" or "secure inside" of a network topology. The notion
of what is inside and outside is totally for the administrator to define.
Logical Objects
Chapter 1: NetDefendOS Overview
24
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...