Logical objects
can be seen as predefined building blocks for use by the rule sets. The address
book, for instance, contains named objects representing host and network addresses.
Another example of logical objects are services which represent specific protocol and port
combinations. Also important are the Application Layer Gateway (ALG) objects which are used to
define additional parameters on specific protocols such as HTTP, FTP, SMTP and H.323.
NetDefendOS Rule Sets
Finally, rules which are defined by the administrator in the various
rule sets
are used for actually
implementing NetDefendOS security policies. The most fundamental set of rules are the
IP Rules
,
which are used to define the layer 3 IP filtering policy as well as carrying out address translation
and server load balancing. The Traffic Shaping Rules define the policy for bandwidth
management, the IDP Rules control the behavior of the intrusion prevention engine and so on.
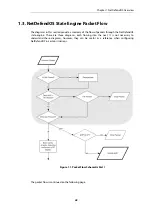
1.2.3. Basic Packet Flow
This section outlines the basic flow in the state-engine for packets received and forwarded by
NetDefendOS. The following description is simplified and might not be fully applicable in all
scenarios, however, the basic principles will be valid for all NetDefendOS deployments.
1.
An Ethernet frame is received on one of the Ethernet interfaces in the system. Basic Ethernet
frame validation is performed and the packet is dropped if the frame is invalid.
2.
The packet is associated with a Source Interface. The source interface is determined as
follows:
•
If the Ethernet frame contains a VLAN ID (Virtual LAN identifier), the system checks for a
configured VLAN interface with a corresponding VLAN ID. If one is found, that VLAN
interface becomes the source interface for the packet. If no matching interface is found,
the packet is dropped and the event is logged.
•
If the Ethernet frame contains a PPP payload, the system checks for a matching PPPoE
interface. If one is found, that interface becomes the source interface for the packet. If no
matching interface is found, the packet is dropped and the event is logged.
•
If none the above is true, the receiving Ethernet interface becomes the source interface
for the packet.
3.
The IP datagram within the packet is passed on to the NetDefendOS Consistency Checker.
The consistency checker performs a number of sanity checks on the packet, including
validation of checksums, protocol flags, packet length and so on. If the consistency checks
fail, the packet gets dropped and the event is logged.
4.
NetDefendOS now tries to lookup an existing connection by matching parameters from the
incoming packet. A number of parameters are used in the match attempt, including the
source interface, source and destination IP addresses and IP protocol.
If a match cannot be found, a connection establishment process starts which includes steps
from here to
9
below. If a match is found, the forwarding process continues at step
10
below.
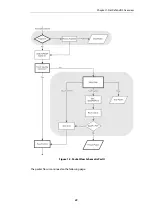
5.
The
Access Rules
are evaluated to find out if the source IP address of the new connection is
allowed on the received interface. If no Access Rule matches then a
reverse route lookup
will
be done in the routing tables.
In other words, by default, an interface will only accept source IP addresses that belong to
networks routed over that interface. A
reverse lookup
means that we look in the routing
tables to confirm that there is a route with this network as the destination on the same
Chapter 1: NetDefendOS Overview
25
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...