certificate and continue.
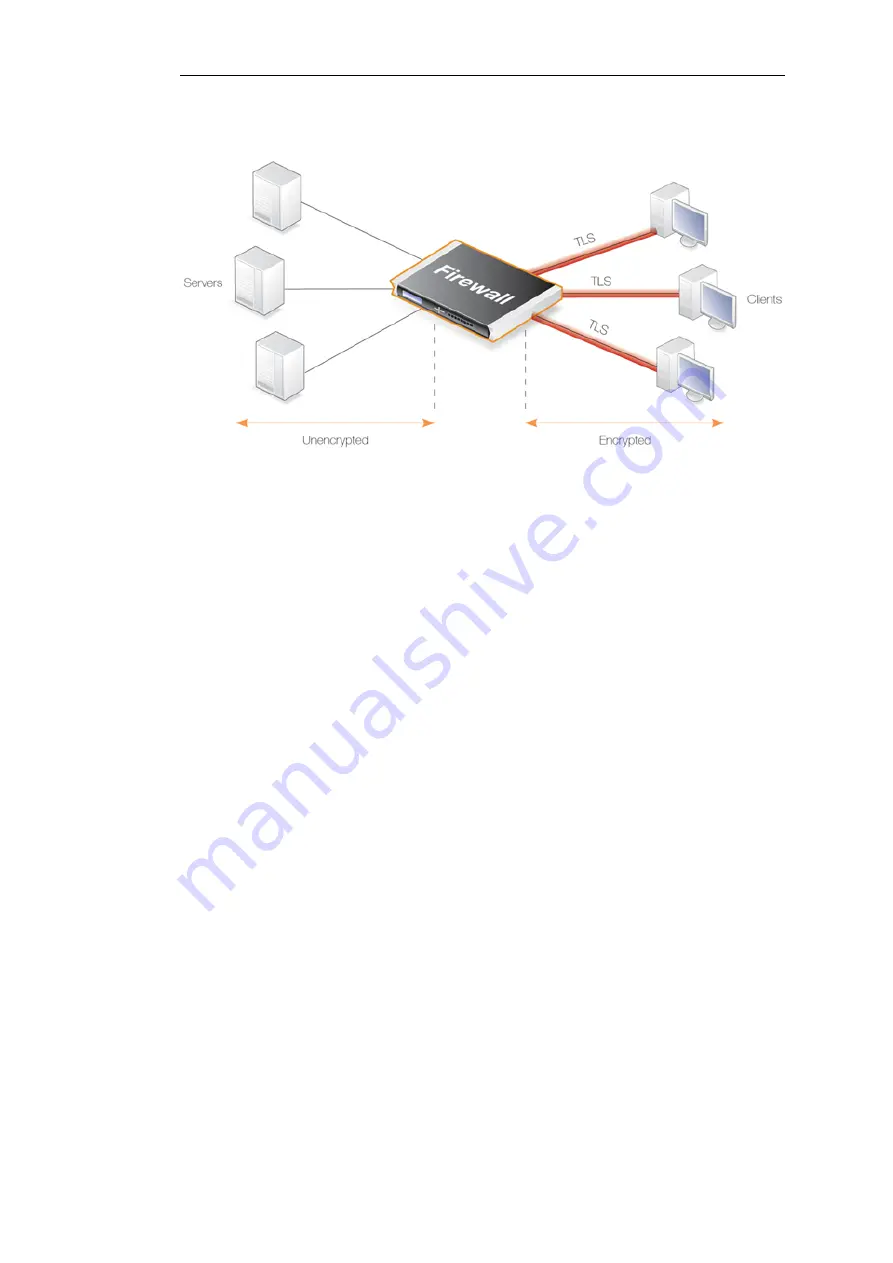
Figure 6.8. TLS Termination
Advantages of Using NetDefendOS for TLS Termination
TLS can be implemented directly in the server to which clients connect, however, if the servers
are protected behind a NetDefend Firewall, then NetDefendOS can take on the role of the TLS
endpoint. NetDefendOS then performs TLS authentication, encryption and unencryption of data
to/from clients and the transfer of unencrypted data to/from servers. The advantages of this
approach are:
•
TLS support can be centralized in the NetDefend Firewall instead of being set up on
individual servers.
•
Certificates can be managed centrally in the NetDefend Firewall instead of on individual
servers. Unique certificates (or one wildcard certificate) does not need to be present on each
server.
•
The encryption/decryption processing overhead required by TLS can be offloaded to the
NetDefend Firewall. This is sometimes referred to as
SSL acceleration
. Any processing
advantages that can be achieved can, however, vary and will depend on the comparative
processing capabilities of the servers and the NetDefend Firewall.
•
Decrypted TLS traffic can be subject to other NetDefendOS features such as traffic shaping or
looking for server threats with IDP scanning.
•
TLS can be combined with NetDefendOS
server load balancing
to provide a means to spread
traffic across servers.
Enabling TLS
The steps to take to enable TLS in NetDefendOS are as follows:
1.
Upload the host and root certificates to be used with TLS to NetDefendOS if not done
already.
2.
Define a new TLS ALG object and associate the appropriate host and root certificates with
Chapter 6: Security Mechanisms
501
Summary of Contents for NetDefendOS
Page 30: ...Figure 1 3 Packet Flow Schematic Part III Chapter 1 NetDefendOS Overview 30 ...
Page 32: ...Chapter 1 NetDefendOS Overview 32 ...
Page 144: ...Chapter 2 Management and Maintenance 144 ...
Page 284: ...Chapter 3 Fundamentals 284 ...
Page 392: ...Chapter 4 Routing 392 ...
Page 419: ... Host 2001 DB8 1 MAC 00 90 12 13 14 15 5 Click OK Chapter 5 DHCP Services 419 ...
Page 420: ...Chapter 5 DHCP Services 420 ...
Page 573: ...Chapter 6 Security Mechanisms 573 ...
Page 607: ...Chapter 7 Address Translation 607 ...
Page 666: ...Chapter 8 User Authentication 666 ...
Page 775: ...Chapter 9 VPN 775 ...
Page 819: ...Chapter 10 Traffic Management 819 ...
Page 842: ...Chapter 11 High Availability 842 ...
Page 866: ...Default Enabled Chapter 13 Advanced Settings 866 ...
Page 879: ...Chapter 13 Advanced Settings 879 ...












































