4 Configuration
D-Link Web Smart Switch User Manual
60
Password –
This parameter should be chosen if the administrator wishes to use an administrator-
defined password for authentication. Upon entry of this parameter, the Switch will prompt the
administrator for a password, and then to re-type the password for confirmation.
Public Key –
This parameter should be chosen if the administrator wishes to use the public key on
an SSH server for authentication.
Host Name:
Enter an alphanumeric string of no more than
32
characters to identify the remote SSH user.
This parameter is only used in conjunction with the
Host Based
choice in the Auth. Mode field.
Host IP:
Enter the corresponding IP address of the SSH user. This parameter is only used in conjunction
with the
Host Based
choice in the Auth. Mode field.
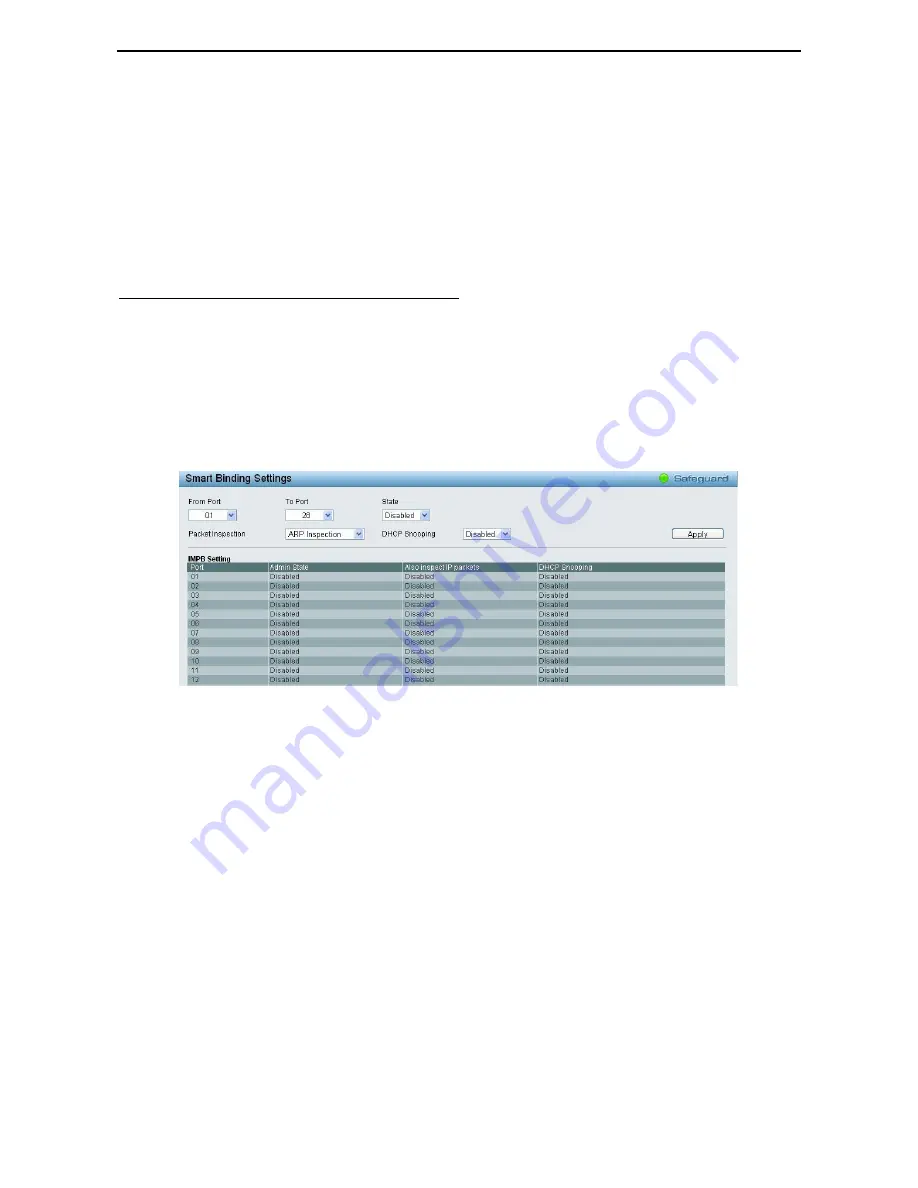
Security > Smart Binding > Smart Binding Settings
The primary purpose of Smart Binding is to restrict client access to a switch by enabling administrators to
configure pairs of client MAC and IP addresses that are allowed to access networks through a switch.
The Smart Binding function is port-based, meaning that a user can enable or disable the function on any
individual port. Once Smart Binding is enabled on a switch port, the switch will restrict or allow client access
by checking the pair of IP-MAC addresses with the pre-configured database, also known as the “IMPB white
list”.
Users can enable or disable the
Inspection packets
and
DHCP Snooping
on the Switch.
Figure 4.88 – Security > Smart Binding > Smart Binding Settings
The Smart Binding Settings page contains the following fields:
From Port/ To Port:
Select a range of ports to set for IP-MAC-port binding.
State:
Use the drop-down menu to enable or disable these ports for Smart Binding.
Enabled –
Enable Smart Binding with related configurations to the ports
Disabled –
Disable Smart Binding.
Packet Inspection:
Specifies
ARP Inspection
or
IP+ARP Inspection
for the IP packets. If ARP inspection is
selected, the Switch will inspect incoming ARP packets and compare them with the Switch’s Smart Binding
white list entries. If the IP-MAC pair of an ARP packet is not found in the white list, the Switch will block the
MAC address. A major benefit of Loose state is that it uses less CPU resources. However, it cannot block
malicious users who send only unicast IP packets. An example of this is that a malicious user can perform
DoS attacks by statically configuring the ARP table on their PC. In this case, the Switch cannot block such
attacks because the PC will not send out ARP packets.
If
ARP+ IP Inspection
mode is selected, the Switch
will inspect all incoming ARP and IP packets and compare them to the IMPB white list. If the IP-MAC pair
find a match in the white list, the packets from that MAC address are unblocked. If not, the MAC address will
stay blocked. While the mode examines every ingress ARP and IP packet, it enforces better security.
DHCP Snooping:
By enable DHCP Snooping, the switch will snoop the packets sent from DHCP Server and
clients, and update information to the White List.
Click
Apply
to make configurations make effects.
















































