xStack
®
DGS-3600 Series Layer 3 Gigabit Ethernet Managed Switch CLI Manual
391
Example usage:
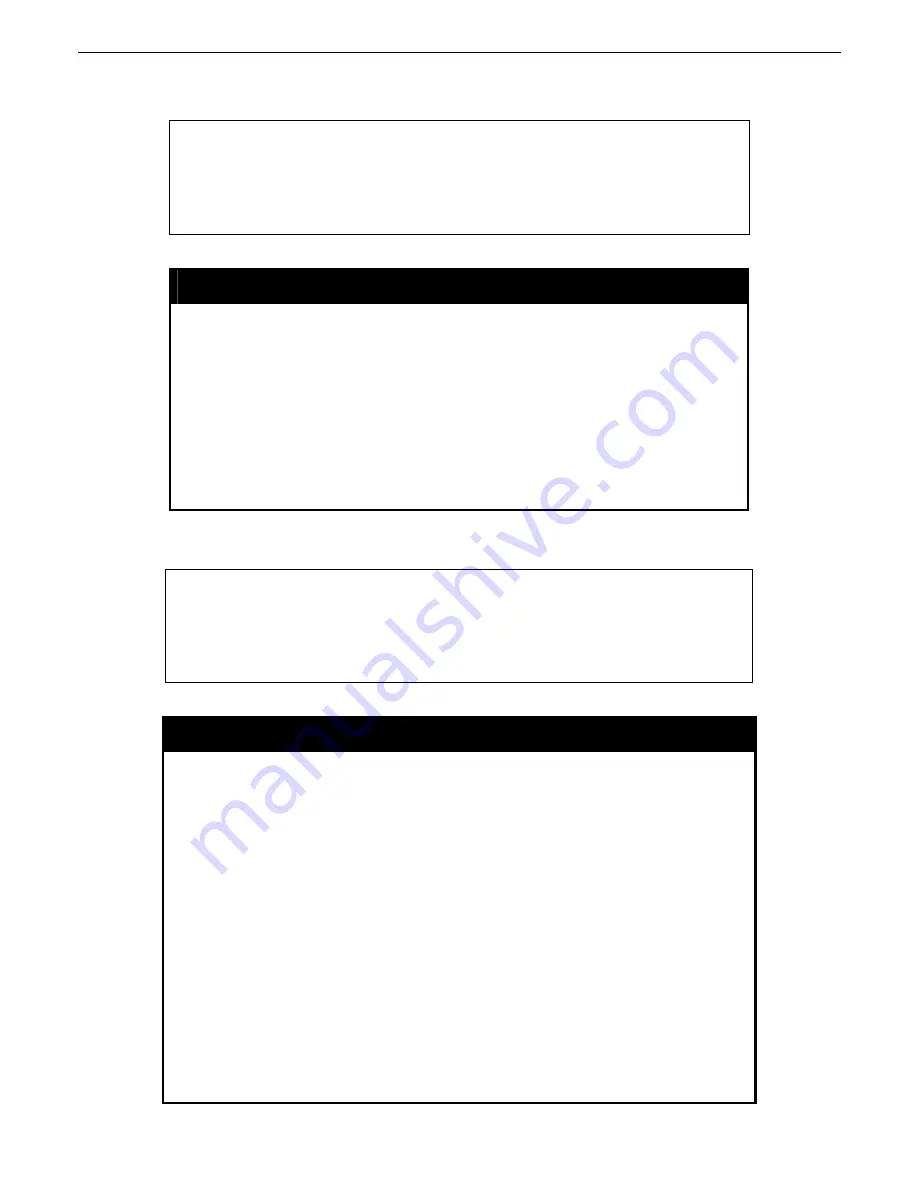
To display the system access authentication policy:
DGS-3627:5#show authen_policy
Command: show authen_policy
Authentication Policy: Enabled
DGS-3627:5#
create authen_login method_list_name
Purpose
Used to create a user defined method list of authentication methods
for users logging on to the Switch.
Syntax
create authen_login method_list_name <string 15>
Description
This command is used to create a list for authentication techniques
for user login. The Switch can support up to eight method lists, but
one is reserved as a default and cannot be deleted. Multiple method
lists must be created and configured separately.
Parameters
<string 15>
– Enter an alphanumeric string of up to 15 characters to
define the given
method list
.
Restrictions
Only Administrator-level users can issue this command.
Example usage:
To create the method list “Trinity.”:
DGS-3627:5#create authen_login method_list_name DLee
Command: create authen_login method_list_name DLee
Success.
DGS-3627:5#
config authen_login
Purpose
Used to configure a user-defined or default
method list
of authentication
methods for user login.
Syntax
config authen_login [default | method_list_name <string 15>]
method {tacacs | xtacacs | | radius | server_group <string
15> | local | none}
Description
This command will configure a user-defined or default
method list
of
authentication methods for users logging on to the Switch. The sequence
of methods implemented in this command will affect the authentication
result. For example, if a user enters a sequence of methods like
tacacs –
xtacacs – local,
the Switch will send an authentication request to the first
tacacs
host in the server group. If no response comes from the server
host, the Switch will send an authentication request to the second
tacacs
host in the server group and so on, until the list is exhausted. At that
point, the Switch will restart the same sequence with the following
protocol listed,
xtacacs
. If no authentication takes place using the
xtacacs
list, the
local
account database set in the Switch is used to authenticate
the user. When the local method is used, the privilege level will be
dependant on the local account privilege configured on the Switch.
Successful login using any of these methods will give the user a “user”
privilege only. If the user wishes to upgrade his or her status to the