xStack
®
DGS-3600 Series Layer 3 Managed Gigabit Ethernet Switch
Database Description packet
Link-State Request packet
Link-State Update packet
Link-State Acknowledgment packet
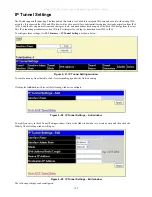
OSPF Packet Header
Every OSPF packet is preceded by a common 24-byte header. This header contains the information necessary for a receiving
router to determine if the packet should be accepted for further processing.
The format of the OSPP packet header is shown below:
OSPF Packet Header
Type
Packet Length
Router ID
Version No.
Area ID
Checksum
Authentication Type
Authentication
Authentication
Figure 4- 39. OSPF Packet Header Format
Field
Description
Version No.
The OSPF version number
Type
The OSPF packet type. The OSPF packet types are as follows: Type
Description Hello Database Description Link-State Request Link-State
Update Link-State Acknowledgment
Packet Length
The length of the packet in bytes. This length includes the 24-byte header.
Router ID
The Router ID of the packet’s source.
Area ID
A 32-bit number identifying the area that this packet belongs to. All OSPF
packets are associated with a single area. Packets traversing a virtual link
are assigned the backbone Area ID of 0.0.0.0
Checksum
A standard IP checksum that includes all of the packet’s contents except for
the 64-bit authentication field.
Authentication Type
The type of authentication to be used for the packet.
Authentication
A 64-bit field used by the authentication scheme.
Hello Packet
Hello packets are OSPF packet type 1. They are sent periodically on all interfaces, including virtual links, in order to establish and
maintain neighbor relationships. In addition, Hello Packets are multicast on those physical networks having a multicast or
broadcast capability, enabling dynamic discovery of neighboring routers.
All routers connected to a common network must agree on certain parameters such as the Network Mask, the Hello Interval, and
the Router Dead Interval. These parameters are included in the hello packets, so that differences can inhibit the forming of
neighbor relationships. A detailed explanation of the receive process for Hello packets is necessary so that differences cannot
inhibit the forming of neighbor relationships.
The format of the Hello packet is shown below:
204