xStack
®
DGS-3600 Series Layer 3 Managed Gigabit Ethernet Switch
Figure 7- 7. ARP Cache Poisoning
When the user configures strict mode and enables IMPB on a port, ARP inspection is enabled. For an ARP inspection active port:
All ARP packets should be captured to the CPU (including broadcast ARP and unicast ARP packets) and the CPU will make the
decision to either forward or drop.
The switch will validate the ARP packets by retrieving the sender’s MAC/ IP address from the ARP packet payload and sender
hardware address. If the IP/ MAC address are in the IMPB forwarding list, the ARP packets will be forwarded. Otherwise, the
ARP packet will be discarded.
Strict State Behavior Change
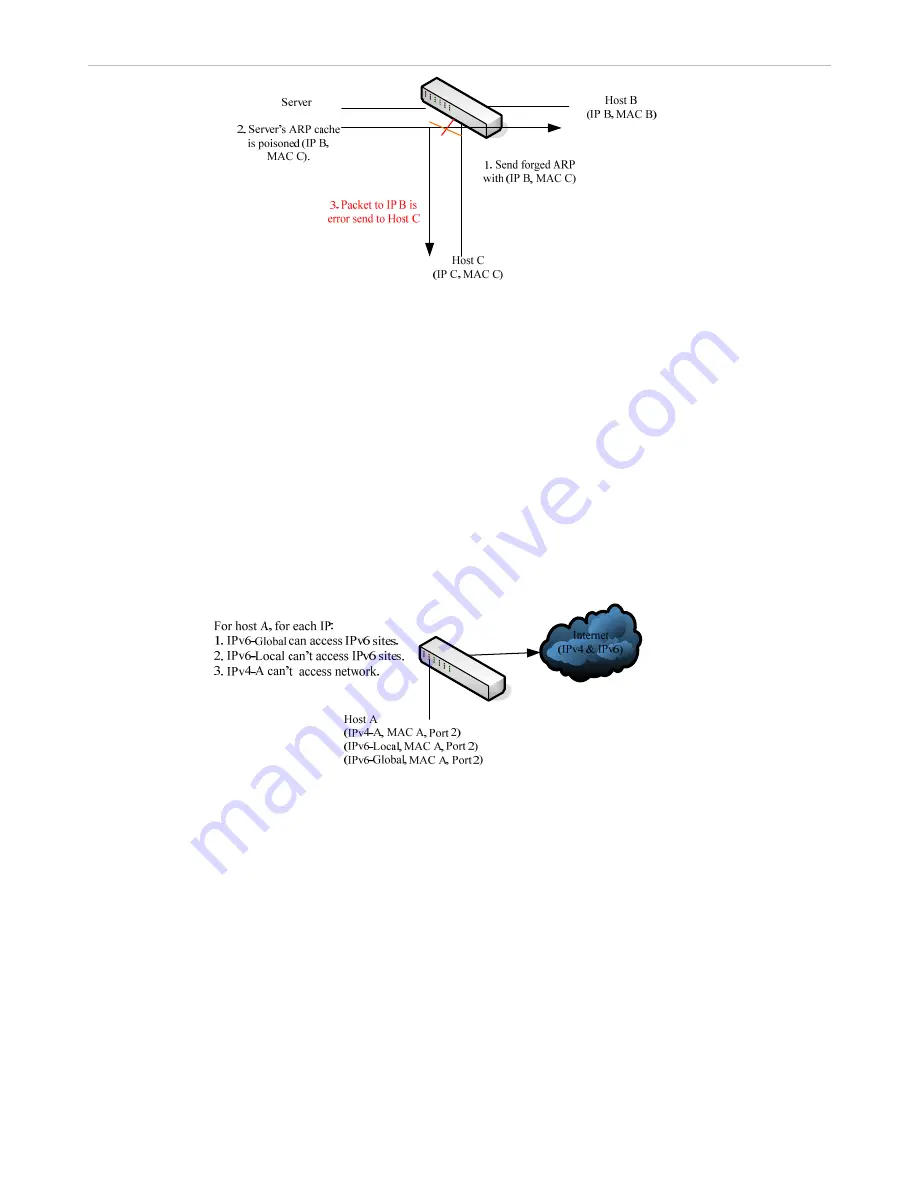
As the figure below shows, in a mixed network (both IPv4 and IPv6 used), if illegal IPv4-A packets are detected and there are
write-blocked FDB entries, then IPv6-Global also cannot access the network. To avoid this case, do not write-block FDB. Not
write-blocking FDB can also avoid netcut attacks and recover attacks.
Figure 7- 8. IPv4 and IPv6 Sharing
When enabling Strict state, the Switch will stop writing dropped FDB entries on these ports. If the Switch detects legal packets,
the Switch will need to create the FDB forwarding entries. ACL mode always runs under Strict state. When a user enables ACL
mode on some ports, these ports will change from Loose state to Strict state and the configuration will also change to Strict state.
For compound authentication And mode (IMPB+1X, IMPB+WAC, IMPB+JWAC), the ports always run in Strict state.
IMPB Global Settings
This window is used to enable or disable IP-MAC-port binding global settings.
To view this window click,
Security
>
IP-MAC-Port Binding
>
IMPB Global Settings
, as shown below:
350