xStack
®
DGS-3600 Series Layer 3 Managed Gigabit Ethernet Switch
Port
The port number of the reauthenticated port.
Auth PAE State
The Authenticator State will display one of the following: Initialize, Disconnected, Connecting,
Authenticating, Authenticated, Aborting, Held, ForceAuth, ForceUnauth, and N/A.
BackendState
The Backend State will display one of the following: Request, Response, Success, Fail, Timeout,
Idle, Initialize, and N/A.
PortStatus
The status of the controlled port can be Authorized, Unauthorized, or N/A.
MAC Address
Displays the physical address of the Switch where the port resides.
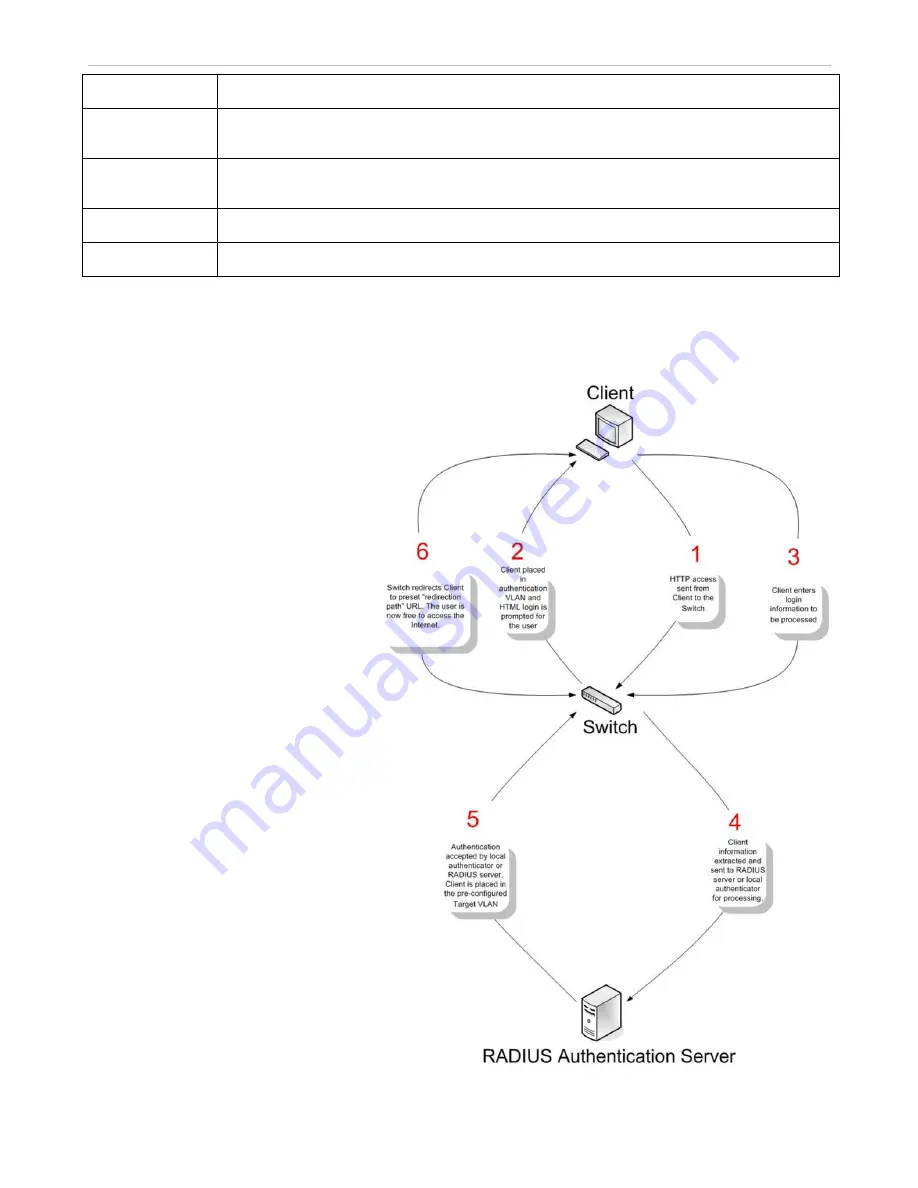
Web-based Access Control (WAC)
Web-based Access Control is another port-
based access control method implemented
similarly to the 802.1X port-based access
control method previously stated. This function
will allow user authentication through a
RADIUS server or through the local
authentication set on the Switch when a user is
trying to access the network via the Switch, if
the port connected to the user is enabled for
this feature.
The user attempting to gain Web access will be
prompted for a user name and password before
being allowed to accept HTTP packets from the
Switch. Once authenticated, the user will be
placed in a target VLAN (if have) on the
Switch where it will have rights and privileges
to openly access the Internet. If denied access,
no packets will pass through to the user.
Once a client has been authenticated on a
particular port, that port will be placed in the
pre-configured VLAN and any other clients on
that port will be automatically authenticated to
access the specified Redirection Path URL, as
well as the authenticated client.
To the right there is an example of the basic six
steps all parties of the authentication go
through for a successful Web-based Access
Control process.
Figure 7- 33. The 6-Step WAC Authentication Process
370