User’s Manual
57
Parameter
Description
Record
By selecting
Record
, the system will record automatically when the alarm is
triggered.
Before enabling this function, you need to configure record period in
Setting >
Storage > Schedule > Record
. For details, see "4.4.1.1 Record Schedule." In
Setting > Storage > Record Control
, select
Auto
for the
Record Mode
.
Record
Delay
The alarm record keeps running for the defined time (from 10 s to 300 s) after
the alarm is ended.
Relay-out
By selecting
Relay-out
, the corresponding alarm output device will be linked
through alarm output port when the alarm is triggered.
Alarm Delay
The alarm keeps running for the defined time (from 10 s to 300 s) after the
alarm is ended.
Send Email
By selecting
Send Email
, the system automatically sends email to the
specified mailbox when the alarm is triggered. You can configure the mailbox
in
Setting > Network > SMTP (Email)
. For details, see " 4.2.7 SNMP."
Snapshot
By selecting
Snapshot
, the system automatically captures images when the
alarm is triggered.
Before enabling this function, you need to configure record period in
Setting > Storage > Schedule > Snapshot
. For tetails, see "4.4.1.2
Click
Save
.
4.3.2
Abnormality
You can set the linkage actions when abnormal events are triggered covering SD card, network,
illegal access, and scene changing.
4.3.2.1
SD Card
When any abnormality happens to the SD card, the alarm will be triggered.
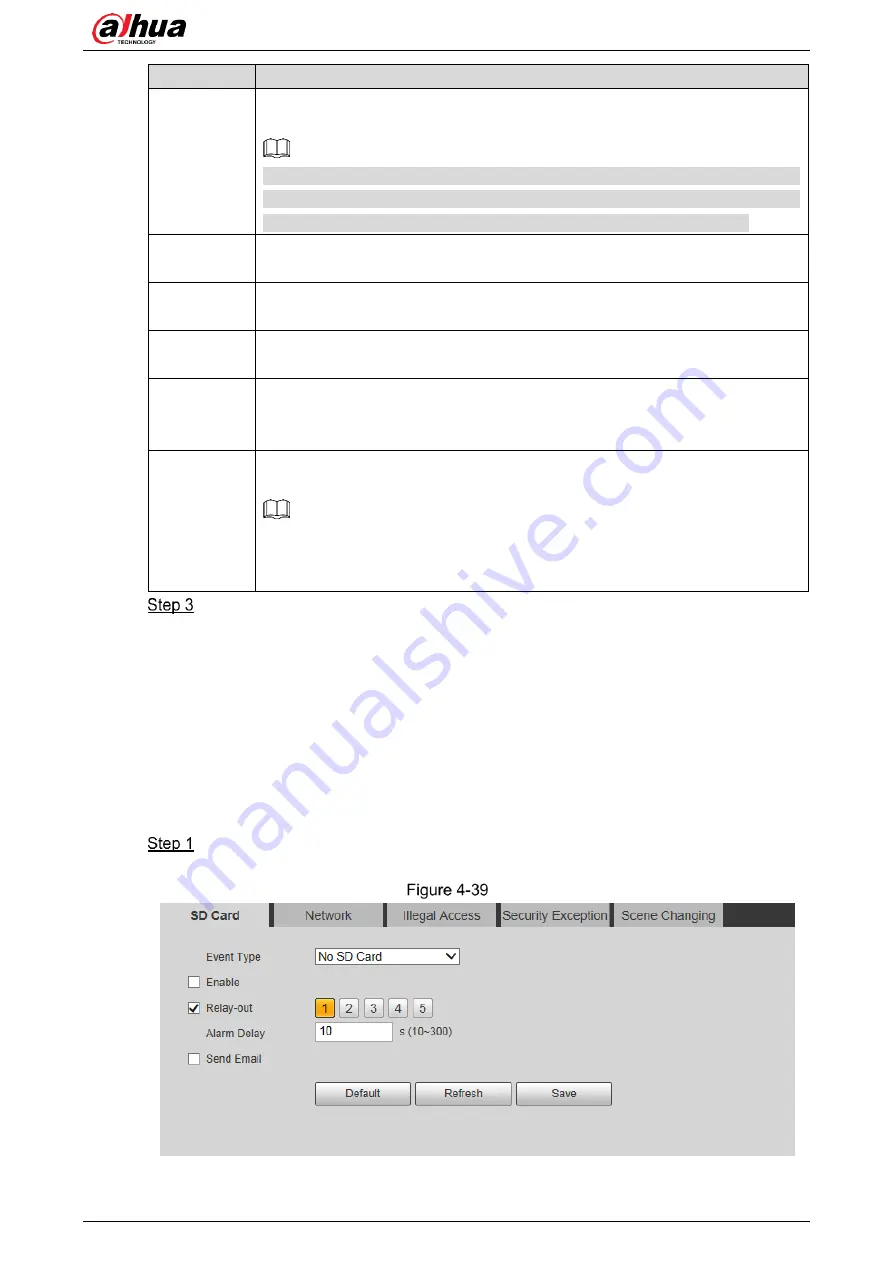
Select
Setting > Event > Abnormality > SD Card
.
The
SD Card
interface is displayed. See Figure 4-39.
SD card
Summary of Contents for DH-PFR4K-E50
Page 31: ...User s Manual 25 Channel title Time title...
Page 32: ...User s Manual 26 OSD information Font...
Page 101: ...User s Manual...
















































