Manual Datafox ZK-Box V4
page 47
date: 16.01.2018 Version: 04.03.06.XX
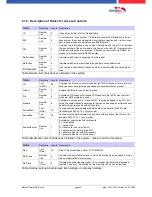
ID
ZM
TM
RefLocation
RefAction
PINGeneral
Reader
1
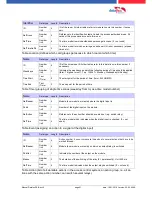
ID
RefGroup
RefTime
RefTimenoPin
Location
3
ID
Weekdays
TimeStart
TimeEnd
Time
4
Day
RefGroup
RefTime
Holiday
5
ID
Group
PIN
Menace
ActiveStart
ActiveEnd
ActiveGeneral
Identification
2
RefReader
PortIn
RefAction
RefTime
Event
6
ID
RefReader
PortOut
Elapse
RefTime
Action
7
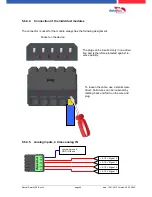
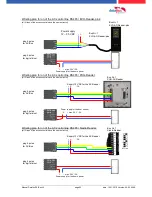
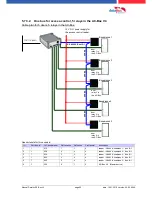
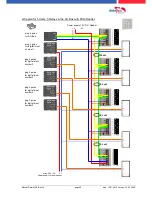
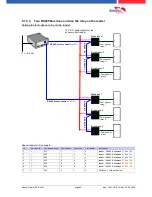
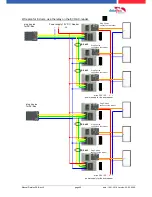
5.7.
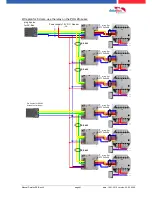
connection and wirering of the accesscontrol
5.7.1. Configuration of Access control adn stuckture
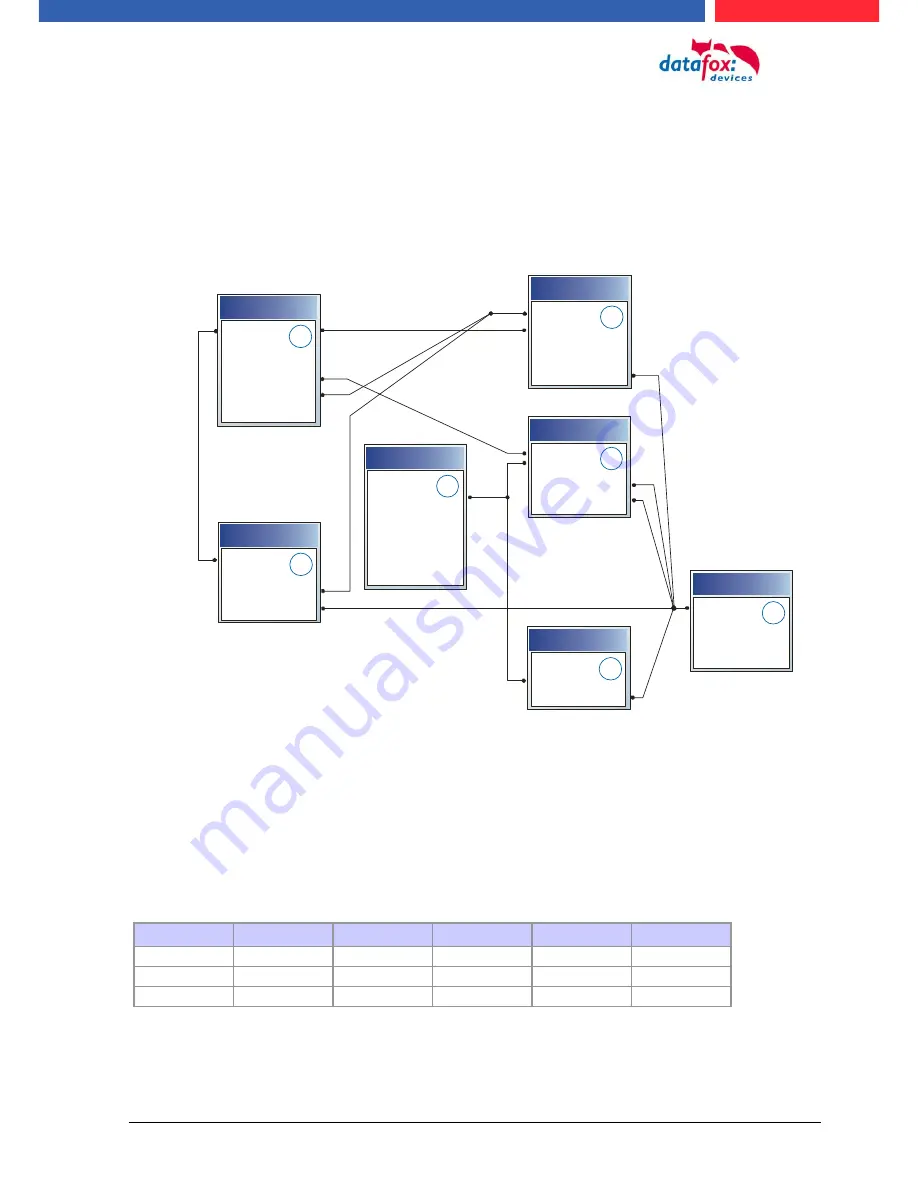
The basis of the access control II are tables. They store all information about the hardware configu-
ration of the access control system, access right of the employees, periods of time (activation,
blocking times, holidays,...). The tables are connected as follows:
The tables are created as text files. For an easier administration you can add comments within the
files.
When adding comments, you have to notice that in a comment line no field values can be given and
that the comment line has to start with a semicolon.
The table Reader.txt might look like this:
ID
ZM
TM
RefLocation
RefAction
PinGeneral
1
1
320
0
1
0
2
1
000
1
2
0
3
1
010
2
3
0