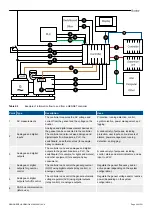
1.2.6 Automatic and remote-controlled starts
The power management system automatically starts gensets when more power is needed. It can be difficult for an inexperienced
operator to predict which gensets will start. In addition, gensets can be started remotely (for example, by using an Ethernet
connection, or a digital input). To avoid personal injury, the genset design, the layout, and maintenance procedures must take this
into account.
1.2.7 Electrostatic discharge
You must protect the equipment terminals from electrostatic discharge when not installed in a grounded rack. Electrostatic discharge
can damage the terminals.
1.2.8 Shelving and taking alarms out of service
DANGER!
Shelved and out of service alarms are completely disabled. These alarms cannot be activated by the operating conditions,
and provide NO protection. Note: Shelving or taking out of service also automatically acknowledges the alarm and resets
the latch.
It is possible to shelve and/or take selected alarms out of service. However, only qualified personnel should shelve and/or take
alarms out of service. This must be done carefully, and only as a temporary measure, for example, during commissioning.
1.2.9 Do not manually override active alarm actions
DANGER!
Do not use switchboard or manual control to override the alarm action of an active alarm.
An alarm may be active because it is latched, or because the alarm condition is still present. If the alarm action is manually
overridden, a latched alarm does not do its alarm action again. In this situation, the latched alarm does not provide protection.
Latched Over-current alarm example
The controller trips a breaker because of over-current. The operator then manually (that is, not using the controller) closes
the breaker while the
Over-current
alarm is still latched.
If another over-current situation arises, the controller
does not trip the breaker again
. The controller regards the original
Over-current
latched alarm as still active, and it does not provide protection.
1.2.10 Do not use unsupported hardware modules
CAUTION
Only use the hardware modules that are listed in the controller data sheet. Unsupported hardware modules can make the
controller malfunction.
1.2.11 Data security
To minimise the risk of data security breaches DEIF recommends:
•
As far as possible, avoid exposing controllers and controller networks to public networks and the Internet.
•
Use additional security layers like a VPN for remote access, and install firewall mechanisms.
•
Restrict access to authorised persons.
DESIGNER'S HANDBOOK 4189340911K UK
Page 23 of 521