768
|
PIM Sparse-Mode
www.dell.com | support.dell.com
Feature Overview
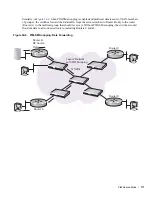
PIM-SM snooping functions in a Layer 2 network in which multiple routers are interconnected by a
switch, such as an IXP where Internet service providers (ISPs) exchange Internet traffic between their
networks. By default, the switch floods multicast traffic to all VLAN member ports, regardless of whether
there are multicast receivers downstream that are joined to a multicast group.
When you enable PIM-SM snooping, the switch receives PIM hello and PIM-SM join/prune messages, and
determines which multicast ports are connected to receivers to which multicast packets should be
forwarded. Multicast data is forwarded only to VLAN member ports on which there are valid downstream
receivers.
•
Using PIM hello messages, the switch learns about PIM neighbors and builds a database for the VLAN
and port on which the packets are received. The PIM Snooping neighbor database is the same one used
for PIM-SM.
Each neighbor entry stores the physical or port-channel port on which a hello message from a neighbor
is received. PIM hello messages are flooded to all VLAN member ports, except the port on which the
message was received. The PIM designated router on the VLAN is learned from the snooped PIM
hello packets.
•
A PIM-SM snooping-enabled switch will proxy the join/prune messages it receives to minimize the
messages it sends upstream. The switch consumes the join/prune messages received from downstream
neighbors and initiates join/prune messages towards upstream neighbors.
All other PIM protocol messages are flooded to VLAN member ports. PIM join/prune messages to
non-existent upstream neighbors are silently dropped.
PIM-SM join/prune messages towards an upstream neighbor are sent only to the port corresponding to
the upstream router in the join message.
PIM (S,G,Rpt) prune and (S,G,Rpt) join messages are snooped and managed according to the PIM-SM
RFC.
•
The switch creates and maintains a tree topology with the state of PIM neighbors in the tree
information base (TIB). Each PIM snooping-enabled VLAN has its own neighbor tree in the TIB.
The PIM (*,G) TIB state maintains the list of multiple upstream neighbors for joins initiated by down-
stream routers towards the rendezvous point (RP). The PIM (*,G,) TIB adds all other upstream neigh-
bor ports to its Outgoing Interface list, except the port to which the join was forwarded, to trigger
assert conditions.
The PIM (S,G) TIB state maintains the list of multiple upstream neighbors for joins initiated by down-
stream routers towards the source.
•
If the PIM designated-router (DR) flood is not disabled (default setting; see
Disable PIM
Designated-Router Flooding on page 772
):
•
Multicast traffic is transmitted on the egress port towards the PIM DR if the port is not the
incoming interface.
•
Multicast traffic for an unknown group is sent on the port towards the PIM DR. When DR flooding
is disabled, multicast traffic for an unknown group is dropped.
•
Multicast traffic for known multicast group addresses, such as Local Network Control Block and
Internetwork Control Block (as defined in RFC 5771), is flooded to all VLAN member ports.
Summary of Contents for Force10 E300
Page 1: ...FTOS Configuration Guide FTOS 8 4 2 7 E Series TeraScale C Series S Series S50 S25 ...
Page 32: ...32 w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 132: ...132 802 1X w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 310: ...310 Configuration Replace and Rollback w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 330: ...330 Dynamic Host Configuration Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 402: ...402 High Availability w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 462: ...462 Interfaces w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 482: ...482 IPv4 Addressing w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 506: ...506 IPv6 Addressing w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 582: ...582 Layer 2 w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 642: ...642 Multicast Source Discovery Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 662: ...662 Multiple Spanning Tree Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 690: ...690 Object Tracking w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 754: ...754 PIM Dense Mode w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 784: ...784 PIM Source Specific Mode w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 800: ...800 Power over Ethernet w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 876: ...876 Quality of Service w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 892: ...892 Routing Information Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1006: ...1006 Simple Network Management Protocol w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1018: ...1018 SONET SDH w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1048: ...1048 Broadcast Storm Control w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1096: ...1096 Uplink Failure Detection UFD w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1098: ...1098 Upgrade Procedures w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1196: ...1196 C Series Debugging and Diagnostics w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1252: ...1252 Standards Compliance w w w d e l l c o m s u p p o r t d e l l c o m ...
Page 1262: ...1262 Index w w w d e l l c o m s u p p o r t d e l l c o m ...