302
Traffic Flow Analyzer - Example | Traffic Flow Analyzer
2
Enable NetFlow on most impacted routers that support NetFlow. Also, register a number of
exporters to enable an efficient and scalable data collection environment.
NOTE:
You can disable NetFlow and unregister exporters.
3
After NetFlow has been running for a while, verify that bandwidth utilization is within
expectation. This will help insure optimum performance of critical business applications.
4
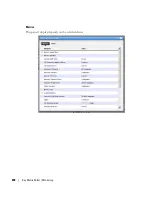
Select the Top 5 Applications portlet (or add it to the page).
5
From the list of the Top 5 Applications, you’ll typically see most bandwidth is being
consumed by the key applications in our organization.
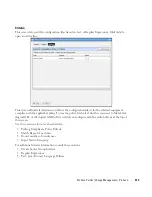
Alternative 1
6
To ensure bandwidth is not being hijacked by unauthorized or unwanted video or music
streaming applications, select the Top 5 Conversations.
7
Often the top conversation is video streaming software.
8
To answer “Where and who is running this rogue application?,” drill down into the
conversation to see End points involved in the conversation. This identifies the user running
the streaming application. You could now go and stop (or block) this rogue application.
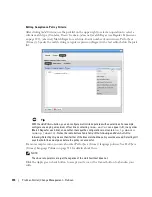
Alternative 2
An alarm indicates port X is surpassing its threshold. If the port has become a bottleneck in the
overall network bandwidth, we want to identify what applications are at cause, and who is
responsible for running them.
1
Look in the Top 5 Traffic Flow Endpoints portlet.
2
From the list of the Top 5 Endpoints, you will typically see that port X is high on the list.
3
Expand the portlet and drill down into the port X endpoint to see what are the top
conversations going through port X.
4
Drill down into conversations to identify any unauthorized applications.
5
Drill down further to identify users of any unauthorized applications
6
Now, go stop them!
Summary of Contents for OpenManage Network Manager
Page 1: ...Dell OpenManage Network Manager version 5 1 Web Client Guide ...
Page 14: ...14 A Note About Performance Preface ...
Page 98: ...98 Schedules Portal Conventions ...
Page 142: ...142 Vendors Key Portlets ...
Page 232: ...232 File Management File Servers ...
Page 242: ...242 Deploy Configuration ...
Page 290: ...290 Key Metric Editor Monitoring Metrics This panel s display depends on the selected device ...
Page 340: ...340 ...
Page 374: ...374 Adaptive CLI Records Archiving Policy Actions and Adaptive CLI ...
Page 380: ...380 Glossary ...
Page 388: ...388 388 Index ...