DPX8000 Series Deep Service Switching Gateway User
Configuration Guide Firewall Service Board Module v1.0
31
3.1.4
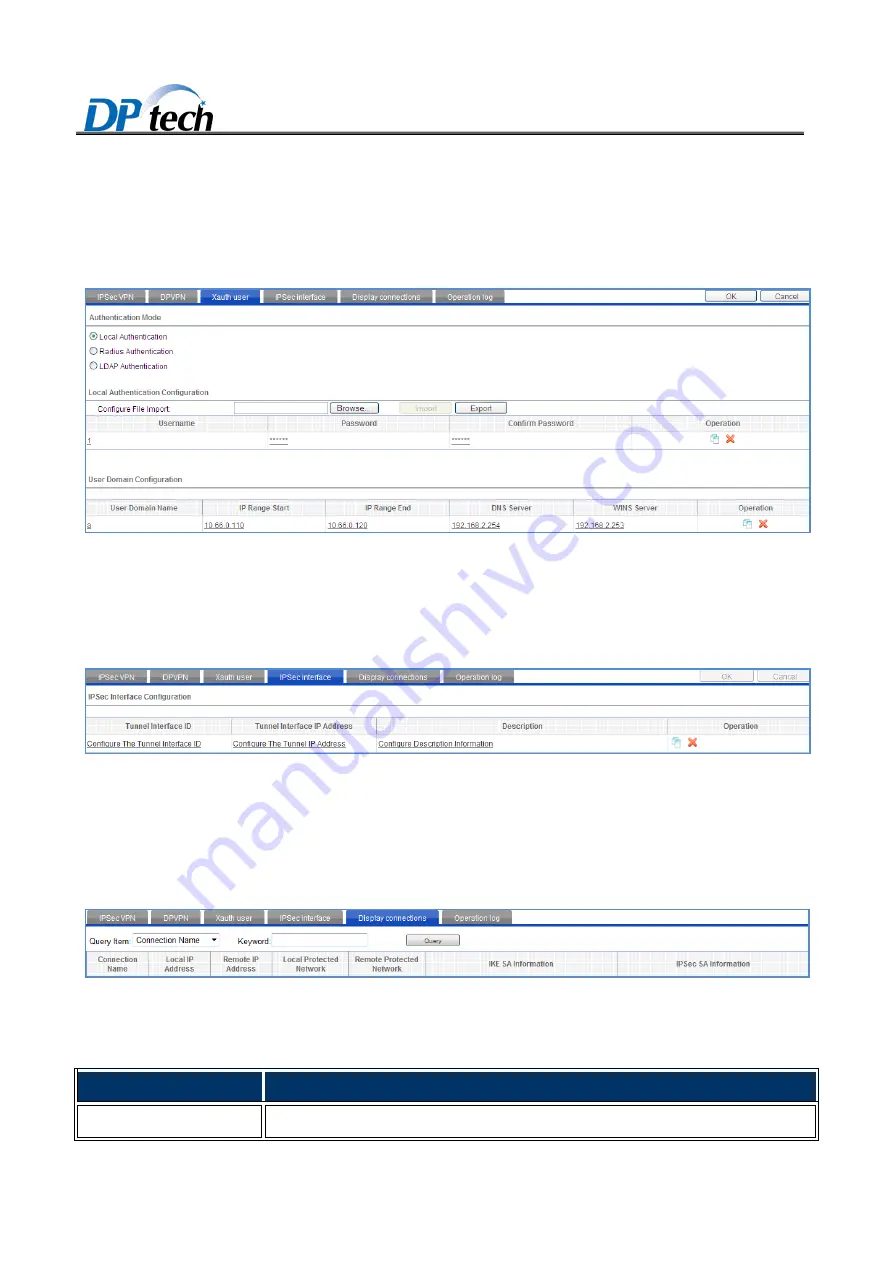
Xauth user
To enter the Xauth user page, you choose
Firewall module > VPN > IPSec > Xauth user
, as shown in Figure3-3.
Figure3-3
Xauth user
3.1.5
IPsec interface
To enter the IPsec page, you choose
Firewall module > VPN > IPsec > IPsec interface
, as shown in Figure3-4.
Figure3-4
IPsec interface
3.1.6
Display connections
To enter the display connections page, you choose
Firewall module > VPN > IPsec > Display connections
, as
shown in Figure3-5.
Figure3-5
Display connection
Table3-3 describes the details of display connections
Table3-3
Display connections
Item
Description
Connection name
Displays connection name of IPsec connection which is configured by users.