DPtech FW1000 Series Firewall Products User Configuration Guide
3-64
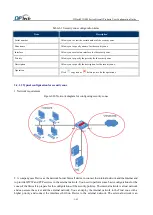
untrusted network, and you need to use strict security rules to control access from the external network to the
internal network and the server. You can deploy the external network in the Untrust zone with a lower priority and
connect the interface gige 0_0 on Device to the external network.
If you deploy the WWW server and the FTP server on the external network, security cannot be ensured; if you
deploy them on the internal network, the external illegal users may use the security holes to attack the internal
network. Therefore, you can deploy the servers in the DMZ zone with a priority between Trust and Untrust, and
connect the Ethernet interface eth0/1 on Device to the servers. In this way, the server in the DMZ zone can access
the external network in the Untrust zone with a lower priority, but when it accesses the internal network in the
Trustzone with a higher priority, its access is controlled by the security rules.
3. Configuration procedure:
By default, the system has created the Trust, DMZ and Untrust zones, defined the priority of these zones.
(1) Deploy the Trustzone.
Select
Basic> Network > Network object > Security zone
from navigation tree to enter the security zone interface,
then select the interface eth0_0 for the trust zone, and then click
Ok
button.
(2) Deploy the DMZ zone.
Select
Basic> Network > Network object > Security zone
from navigation tree to enter the security zone interface,
then select the interface eth0_1 for the DMZ, and then click Ok button.
(3)Untrust zone
Select
Basic> Network > Network object > Security zone
from navigation tree to enter the security zone interface,
then select the interface eth0_7 for the Untrust zone, and then click Ok button.
3.4.2 IP address
3.4.2.1 Introduction to IP address
IP address function provides user with address object, address object group function for users. Those functions can
divide the inner network addresses into several groups and apply these addresses to the expanded application, so that
the inner network user can be managed effectively.
3.4.2.2 IP address object
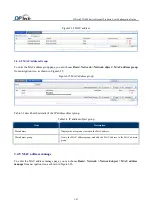
To enter the IP address object page, you can choose
Basic> Network > Network object > IP address > IP address
object
from navigation tree
,
as shown in Figure3-21.