DPtech FW1000 Series Firewall Products User Configuration Guide
3-123
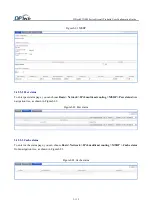
Figure3-105
Policy-based routing
Table3-50 describes the configuration items of policy-based routing.
Table3-50
Policy-based routing configuration items
Item
Description
ID
Displays the sequence number of the PBR policy.
Source subnet
Allows you to configure the source IP address of the PBR policy.
Destination subnet
Allows you to configure the destination IP address of the PBR policy.
ToS
Allows you to configure the type of service (ToS).
Inbound interface
Allows you to select which interface enabled the PBR policy.
Protocol
Allows you to select which protocol should be used by the PBR policy
Nexthop
Allows you to configure nexthop information.
Operation
Click
copy or
delete or
insert icon to do the operations.
3.14.3.2 Monitoring
To enter the monitoring page, you can choose
Basic> Network >Policy-based routing > Monitoring
from
navigation tree, as shown in Figure3-106.