DPtech WCS 7000 Series Wireless Access Controller User Configuraiton Guide
82
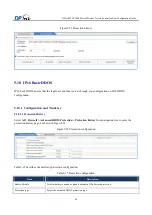
Table5-11
Basic attack log query
Item
Description
Serial number
Displays serial number of the attack.
Time
Displays when the attack log is created.
Attack type
Displays the type of the attack.
Protocol
Displays the protocol of the attack.
Source IP
Displays the source IP of the attack.
Destination IP
Displays the attack packet destination IP address.
Source port
Displays the interface of the attack.
Action
Displays the action for the attack.
To query the basic attack log query:
In each item, enter the parameter that you want to query
Click
Query
button, then you can view the searching result that you have queried
Click
Export
button, then you can export the basic attack log file to the remote system
Click
Delete
button, then you can delete all logs that you have searched.
5.7 Session Limit
Select
AC> Advance > Sessions Limit
from navigation tree to enter the session limit page, as shown in Figure5-16.
Figure5-16
Sessions Limit
5.8 Service Limit
Select
AC > Advance >Service Limit
from navigation tree to enter the service limit page, as shown in Figure5-17.