Cybersecurity considerations for electrical distribution systems
Securing the Network Management Module – 197
•
•
•
•
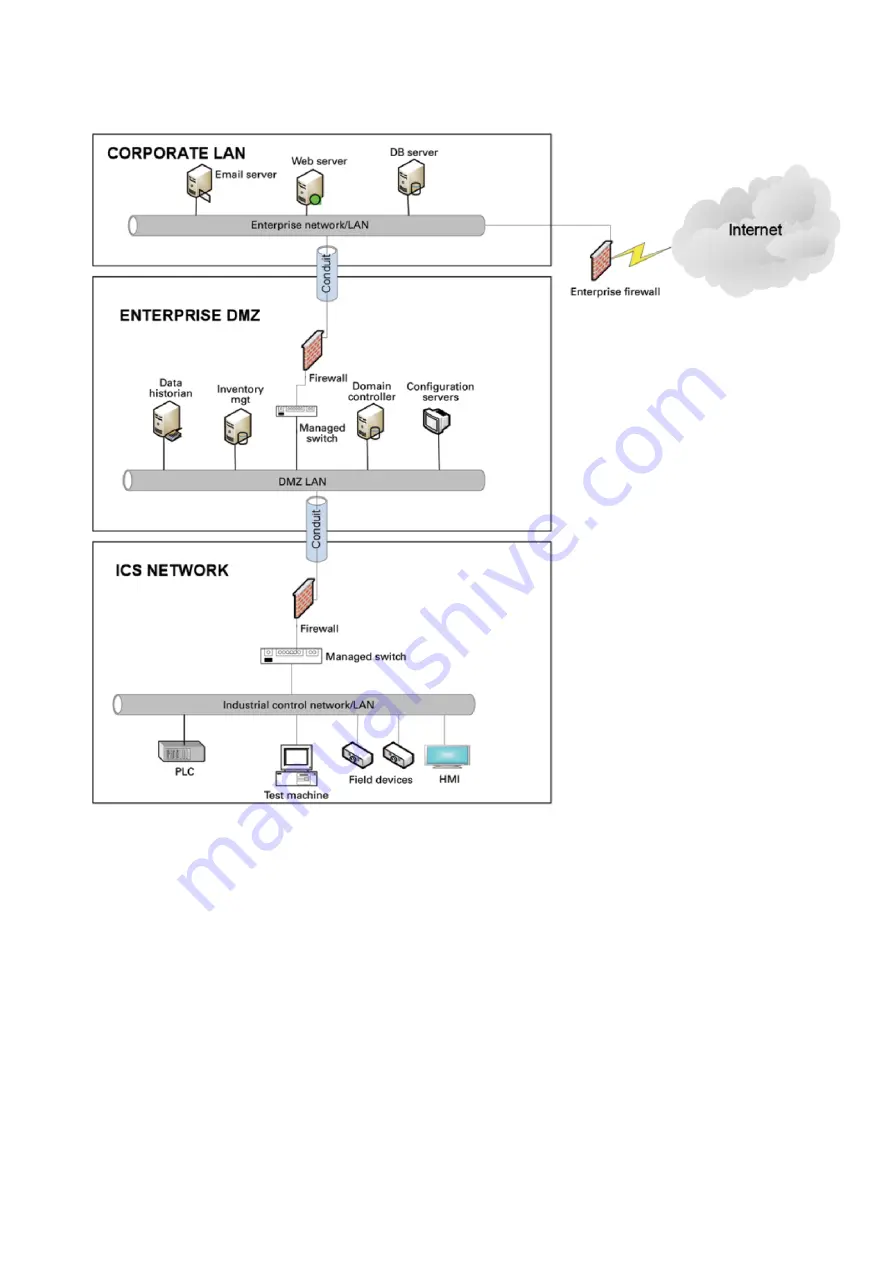
5.1.6.2.1 Three-tier architecture for a secure control network
Above figure shows that the control networks are divided into layers or zones based on control functions, which are then
connected by conduits (connections between the zones) that provide security controls to:
Control access to zones
Resist denial of services (DOS) attacks or the transfer of malware
Shield other network systems
Protect the integrity and the confidentiality of network traffic
Beyond network segmentation, access control (both physical and logical) should be defined and implemented.
The key consideration when designing access control is defining the required interactions both within a given zone and between
zones. These interactions should be mapped out clearly and prioritized based on need. It is important to realize that every hole
poked in a firewall and each non-essential functionality that provides access or creates additional connectivity increases potential
exposure to attacks. A system then becomes only as secure as the devices connecting to it.
If mapped correctly, the potential adverse impact to control system reliability and functionality should be negligible. However, this
element introduces additional costs (in terms of firewall and other network infrastructure) and complexity to the environment.
Summary of Contents for INDGW-X2
Page 1: ...UPS Industrial Gateway Card INDGW X2 User s Guide English 10 18 2021 2 2 3 ...
Page 23: ...Configuring Modbus Installing the Network Management Module 25 ...
Page 24: ...Configuring Modbus Installing the Network Management Module 26 ...
Page 25: ...Configuring Modbus Installing the Network Management Module 27 ...
Page 26: ...Configuring Modbus Installing the Network Management Module 28 ...
Page 35: ...Home Contextual help of the web interface 37 3 2 7 1 3 Battery mode 3 2 7 1 4 Off mode ...
Page 37: ...Home Contextual help of the web interface 39 3 2 7 2 2 Bypass mode 3 2 7 2 3 Battery mode ...
Page 61: ...Protection Contextual help of the web interface 63 Example 4 Custom ...
Page 62: ...Protection Contextual help of the web interface 64 Settings 1 Settings 2 ...
Page 218: ...Default settings and possible parameters Information 220 ...
Page 266: ...Acronyms and abbreviations Information 268 ...
Page 273: ......
















































