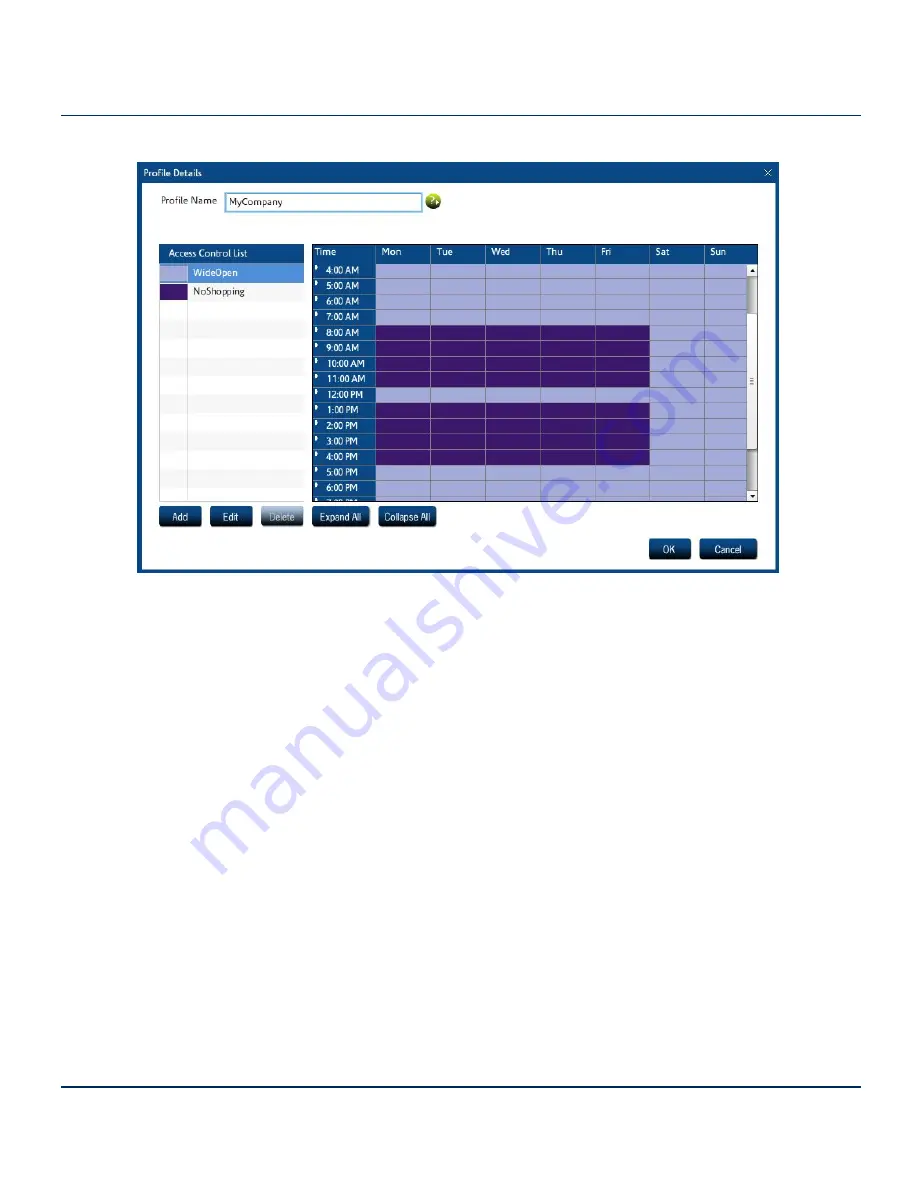
Figure 1. Profiles and Scheduling
In this example, the schedule applies to the entire company (Profile name = MyCompany). But
sometimes you need to give different users different access rights. For example, the Purchasing
department may legitimately need access to online shopping, and Finance may need access to
online gambling. In addition, upper management and iPrism administrators may have access to
everything.
iPrism uses two different types of profiles:
•
Web Profiles are used to filter web surfing or HTTP/HTTPS traffic.
•
Application Profiles filter IM and P2P usage.
Each profile is associated with a group of users. One way of identifying users is by the IP address of
the machine they are using. For example, you can define a profile called “Sales”, which is mapped to
the IP addresses in the range 192.168.77.0 to 192.168.77.255.
Users can also be identified by a username and password through an authentication process. There
are a number of authentications available including NTLM (for Microsoft Windows users), Kerberos
(for Microsoft Windows and Macintosh users) and LDAP (for Macintosh, UNIX, Linux, and Novell
users).
Chapter 2 Overview
6
iPrism
Administration Guide