7.
To download the Remote Filtering client software, click Download Client Software. This will
take you to a website where you can complete the download. For more information about
configuring and using iprism_Client_Auth.key, refer to the
iPrism Remote Filtering Client Guide
.
8.
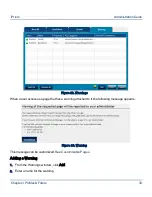
Click Exceptions to define specific network ranges or ports for which filtering on the remote client
will not be enforced.
•
Specify the target network ranges (IP address and Netmask) you do not want to monitor for
remote users, in Unmonitored Network Ranges.
•
Specify the range of target ports you do not want to monitor for remote users, in
Unmonitored Ports.
•
Click OK.
Figure 30. Remote Filtering Exceptions
9.
Remote clients that are controlled by a policy in which monitoring is configured periodically send
event logs back to iPrism by way of the EdgeWave Data Center. The frequency at which iPrism
requests events from the Data Center can be adjusted with the Remote Filtering Logs
selection. To initiate an immediate log retrieval (i.e., not wait for the next cycle), click Initiate Log
Download.
10.
When you are finished on this page, click Save.
Chapter 3 Profiles & Filters
51
iPrism
Administration Guide