Figure 50. Managing Exceptions
2.
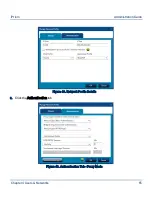
Type a name for the exception in the Name field.
3.
Select the type of exception:
•
No Filter: Traffic will pass unfiltered through the specified Source and Destination range of
IP addresses, or the specified port.
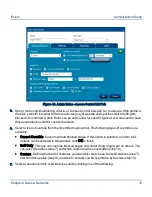
•
Block: Traffic destined for the specified IP address range OR the specified port(s) will be
blocked.
•
NAT (Network Address Translation): NAT replaces the IP address of the sender (i.e., the
user) with the IP address of iPrism, for outbound traffic. A reverse translation is done to any
responses coming back. The effect of NAT is that requests look like are coming from iPrism
only. This setting hides the IP addresses of your internal workstations from the Internet
(transparent mode only).
•
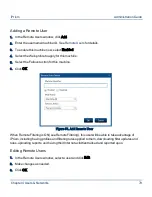
No Authentication: Traffic destined for the IP address range will not be authenticated.
•
No Authentication & NAT: Combines NAT with No Authentication in one option.
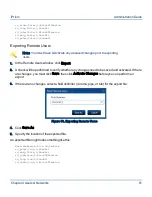
Note: Exception types are applied in order of priority based on the type. For
example, if a “No Filter” exception has been created for an IP address range,
and later a subsequent “Block” exception is created for that same IP address
range, the “No Filter” exception wins, as iPrism encounters that type of
exception first; thus, traffic will pass unfiltered through that IP address range.
Chapter 4 Users & Networks
76
iPrism
Administration Guide