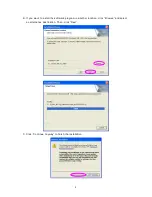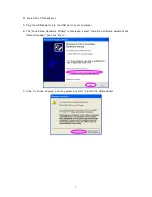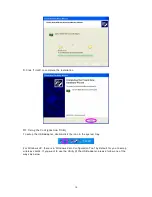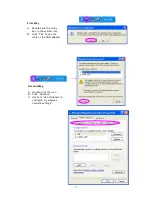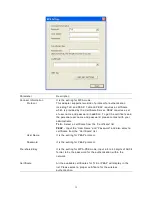
Parameter Descriptio n
Key1 ~ Key4
The keys are use d to encrypt data transmitted in the wireless
network. Fill the text bo x by following the rules below.
64-bit
– Input 10-dig it He x values or 5-digit ASCII values as the
encryptio n keys. For exa mple: “0123456aef“ or “Guest“.
128-bit
– Inp ut 26-digit He x va lues or 13-digit ASCII values as the
encryptio n keys. For exa mple:
“012345678901234 56789abcd ef“ or “administrator“.
256-bit
– Inp ut 58-digit He x va lues or 29-digit ASCII values as the
encryptio n keys.
Cha nge/App ly
Clcik “Cha ng e“ will ena ble yo u to setup the WEP key. In the
mea ntime, the b utton will c ha nge to “Apply“ for you to confirm
your settings.
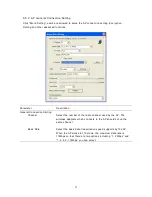
6.3.2 WPA Setting
The adapter ca n auto matically detect the WPA setting of the AP whic h t he adapter inte nds
to connect to. To connect to the AP, you s ho uld setup t he same setting with the AP.
There are two kinds of WPA mode: WPA and WPA-PSK. WPA is desig ned for enterprise
whic h req uires a RADI US Server and Certificate Server for the aut he nticatio n. WPA-PSK is
a special mode des ig ned for ho me and small b usiness users who do not ha ve access to
network authe nticatio n servers. In this mode, the user ma nua lly e nters the starting
password in their access point or gateway, as well as in eac h wireless stations in t he
network. WPA takes over automatically from that point, keeping una ut horized users that
don't ha ve the matc hing password from joining the network, while e ncrypting the data
traveling between a uthorized devices.
18