12
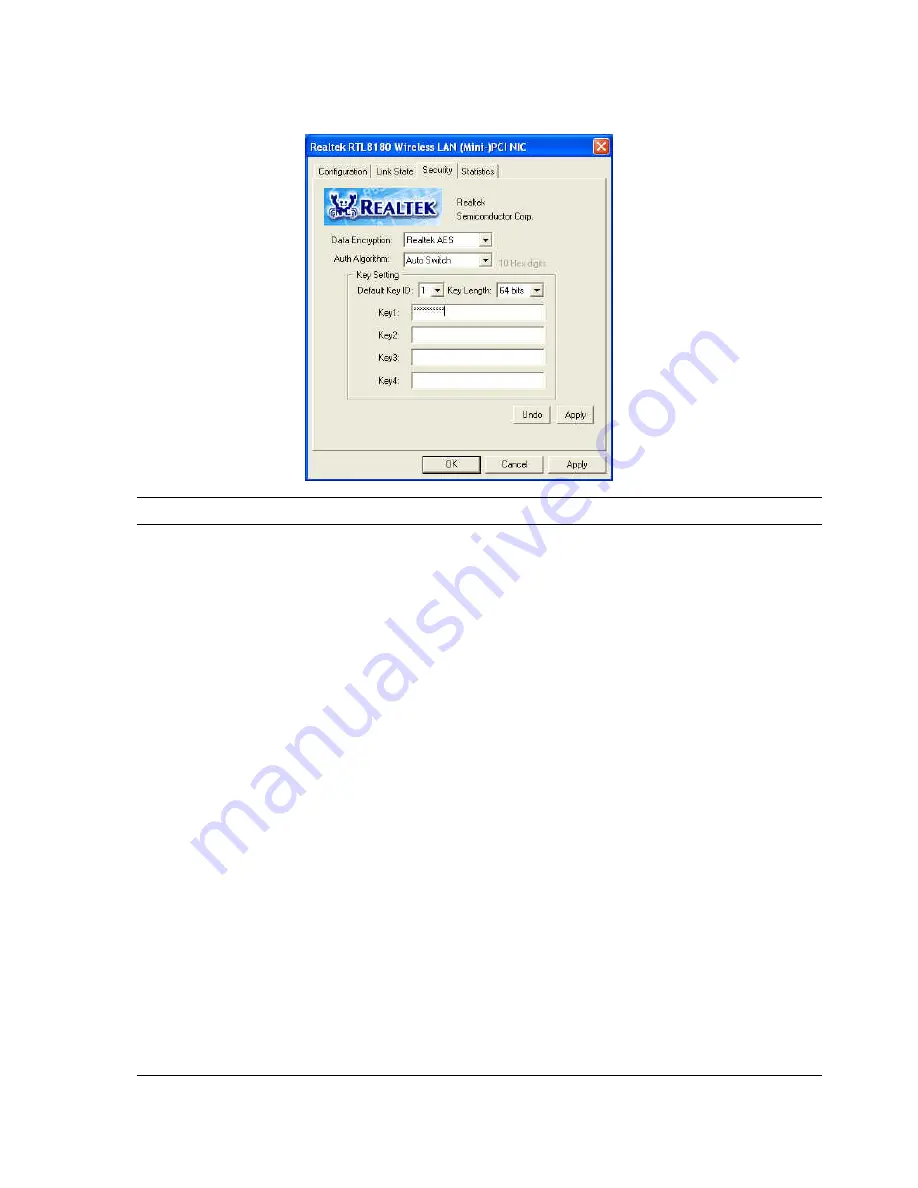
Parameter Description
Data Encryption
•
No Encryption –
Disable the WEP Data Encryption.
•
WEP –
Enable the WEP Data Encryption. When the item is
selected, you have to continue setting the WEP Key Length
and the encryption keys.
•
Realtek TKIP –
Enable the TKIP Data Encryption. When the
item is selected, you have to continue setting the TKIP Key
Length and the encryption keys.
•
Realtek AES –
Enable the AES Data Encryption. When the
item is selected, you have to continue setting the AES Key
Length and the encryption keys.
Auth Algorithm
This setting has to be consistent with the wireless devices which
the adapter intends to connect.
•
Open System –
No authentication is needed among the
wireless devices.
•
Shared Key –
Only wirelss devices using a shared key (WEP
Key, TKIP Key or AES Key identified) are allowed to
connecting each other. Setup the same key as the wireless
devices which the adapter intends to connect.
•
Auto Switch –
Auto switch the authentication algorithm
depending on the wireless devices which the adapter is
connecting to.
Default Key ID
Select one of the keys (1~4) as the encryption key.