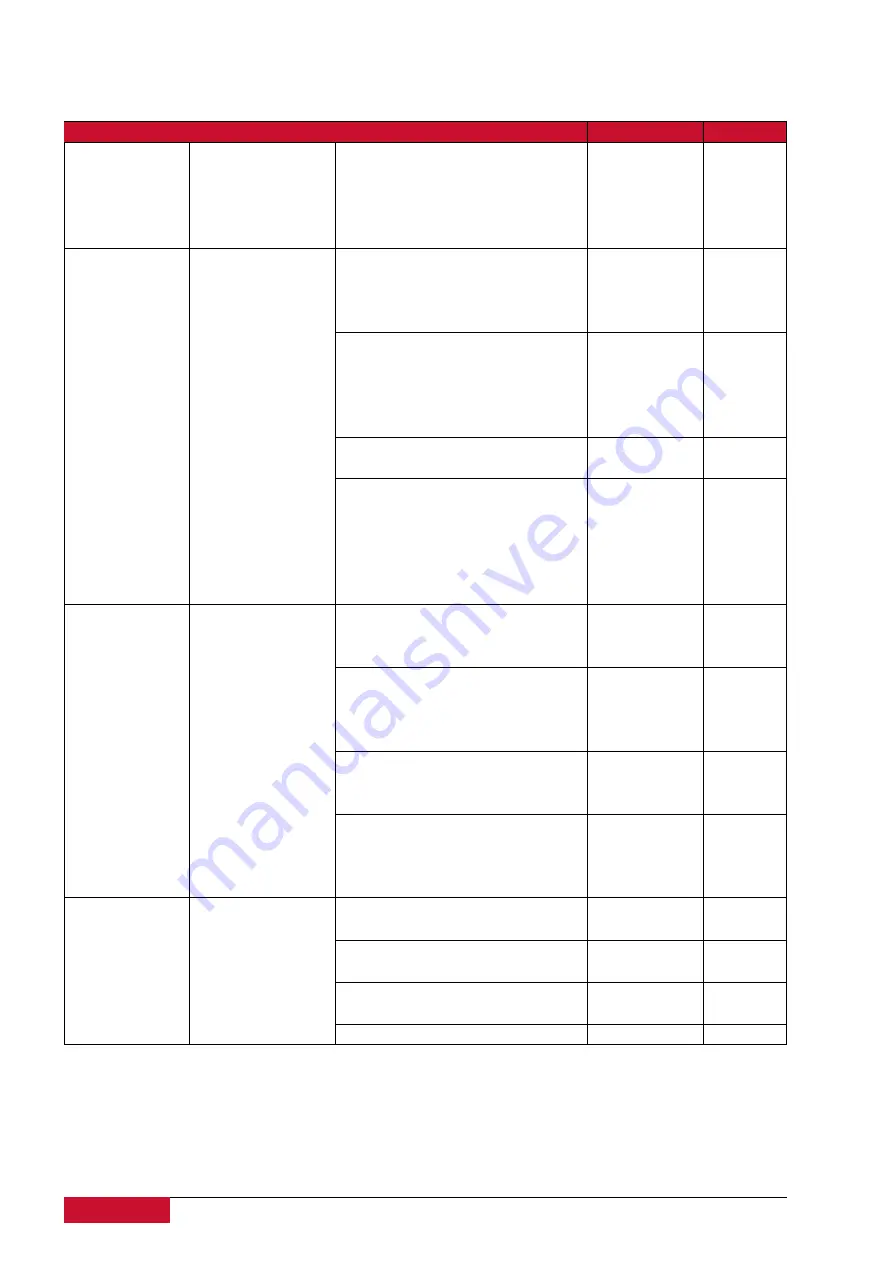
Table 40: Conformance to IEC 62351 standard
Standard
Description
Topic
Implemented
Version
IEC 623518
Rolebased
access control
Covers the access control of
users and automated agents to
data objects in power systems
by means of rolebased access
control (RBAC)
Yes
>=1.2.6
IEC 623519
Key
Management
Describes
the
correct
and
safe
usage
of
safetycritical
parameters, e.g.
passwords,
encryption keys.
No
Covers the whole life cycle of
cryptographic
information
(enrolment,
creation,
distribution, installation, usage,
storage and removal)
No
Methods for algorithms using
asymmetric cryptography
No
A
secure
distribution
mechanism based on GDOI
and
the
IKEv2
protocol
is
presented for the usage of
symmetric keys, e.g.
session
keys.
No
IEC 6235110
Security
Architecture
Explanation
of
security
architectures
for
the
entire
IT infrastructure
No
Identifying critical points of the
communication
architecture,
e.g.
substation control center,
substation automation
No
Appropriate
mechanisms
security requirements, e.g. data
encryption, user authentication
No
Applicability
of
wellproven
standards from the IT domain,
e.g.
VPN tunnel, secure FTP,
HTTPS
No
IEC 6235111
Security for XML
Files
Embedding of the original XML
content into an XML container
No
Date of issue and access control
for XML data
No
X.509 signature for authenticity
of XML data
No
Optional data encryption
No
156




































