User Authentication
3-73
3
Web
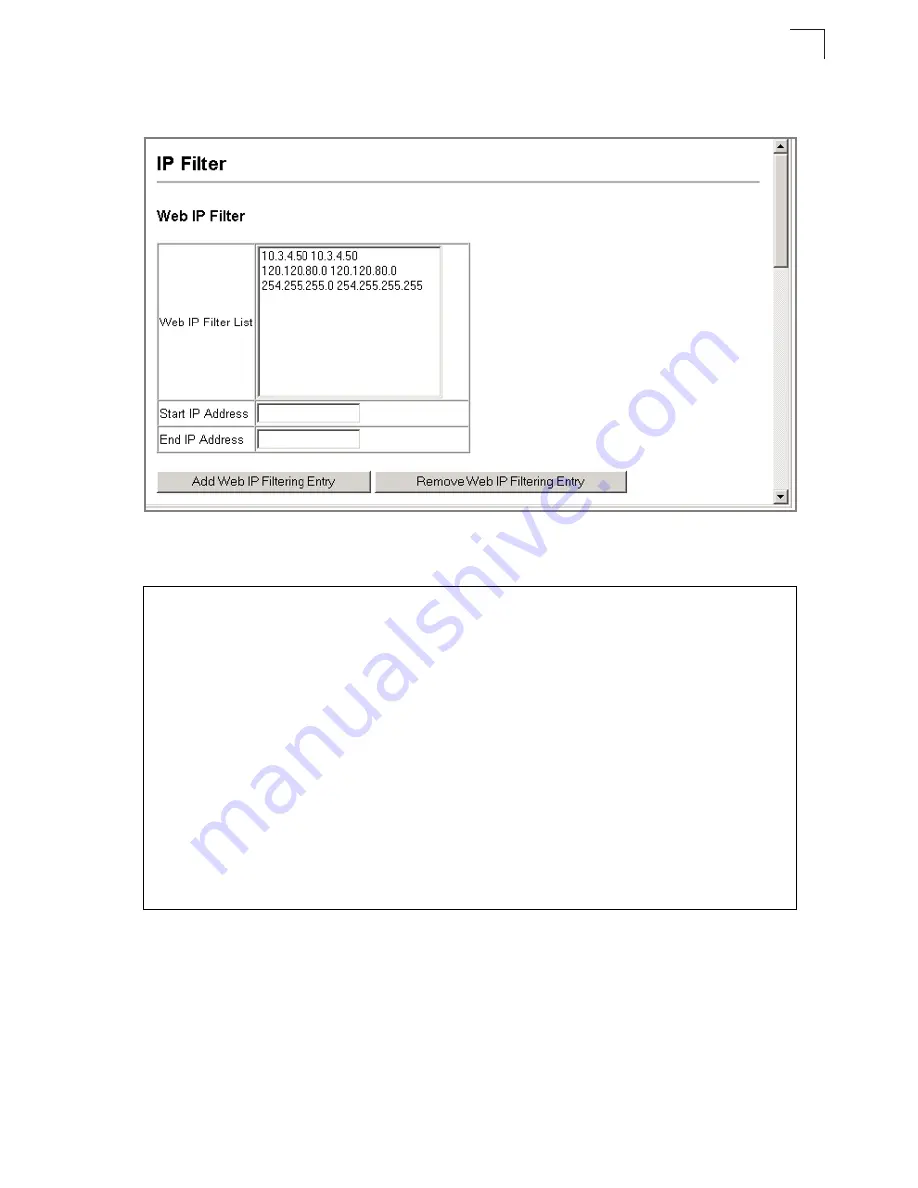
– Click Security, IP Filter. Enter the addresses that are allowed management
access to an interface, and click Add IP Filtering Entry.
Figure 3-45. Entering IP Addresses to be Filtered
CLI
– This example restricts management access for Telnet and SNMP clients.
Console(config)#management telnet-client 192.168.1.19
4-28
Console(config)#management telnet-client 192.168.1.25 192.168.1.30
Console(config)#management snmp-client 10.1.2.3 255.255.255.255
4-28
Console(config)#end
Console#show management telnet-client
4-29
Management IP Filter
TELNET-Client:
Start IP address End IP address
-----------------------------------------------
1. 192.168.1.19 192.168.1.19
2. 192.168.1.25 192.168.1.30
Console#show management snmp-client
4-29
Management IP Filter
SNMP-Client:
Start IP address End IP address
-----------------------------------------------
1. 10.1.2.3 255.255.255.255
Console#
Summary of Contents for Matrix-V V2H124-24P
Page 2: ......
Page 8: ...Notice vi...
Page 22: ...Contents xx...
Page 26: ...Tables xxiv...
Page 30: ...Figures xxviii...
Page 38: ...Introduction 1 8 1...
Page 50: ...Initial Configuration 2 12 2...
Page 159: ...Port Configuration 3 109 3 Figure 3 66 Displaying Etherlike and RMON Statistics...
Page 234: ...Configuring the Switch 3 184 3...
Page 480: ...Command Line Interface 4 246 4...
Page 496: ...Index Index 4...
Page 497: ......
Page 498: ...Part 150200039400A FW 2 5 2 0 E012005 R02 ES3526G E072000 R04...
















































