Pearl-2 User Guide
Configure 802.1x network security and manage user
certificates
4. (Optional) Check
Verify server's identity
.
5. Choose an
Authentication method
if you selected EAP-TTLS as the EAP method. The authentication
method is automatically selected if PEAP or EAP-TLS is the EAP method.
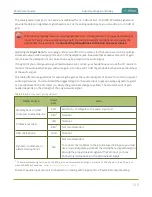
Table 24
Authentication methods
EAP method
Authentication method
PEAP
EAP-MSCHAPv2
EAP-TLS
TLS
EAP-TTLS
EAP-MSCHAPv2
TLS
PAP
6. Enter the network access
User name
and
Password
to use for this device. Available fields depend on
the EAP method that is selected.
7. If
TLS
is chosen as the Authentication method, upload a user certificate and a user private key. You can
request those from your network administrator.
125