Exinda Network Orchestrator
3 Using
|
315
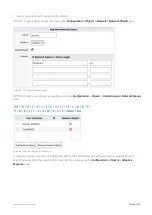
Note that both virtual circuits can be specified as requiring 100% of the available bandwidth with automatic handling of
over-subscription. This allows the bandwidth to be shared. However, since unauthenticated traffic requires very little
bandwidth, the authenticated users will get almost all of the bandwidth.
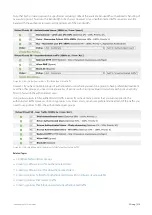
Screenshot 142: Using virtual circuits to filter for authenticated traffic
However, if you have multiple groups of authenticated users where you want one group to have preferential treatment
over the other groups, you need to create a series of policies within a single virtual circuit where each policy explicitly
filters in favour of the authenticated users.
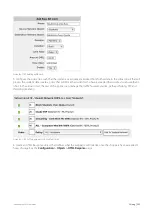
Using virtual circuits to filter authenticated traffic is easier if you have many policies that you want applied to the
authenticated traffic. However, since only policies, not virtual circuits, can ensure preferential treatment of the traffic, you
need to use policies to filter the authenticated user groups.
Screenshot 143: Using the policies themselves to filter for authenticated traffic
Related Topics
Creating a Virtual Circuit for Authenticated Users
Creating a Virtual Circuit for Unauthenticated Users
Creating policies to filter for Authenticated Users with no Virtual Circuit available
Creating policies that redirect traffic
Creating policies that block unwanted unauthenticated traffic
Summary of Contents for EXNV-10063
Page 369: ...Exinda Network Orchestrator 4 Settings 369 ...
Page 411: ...Exinda Network Orchestrator 4 Settings 411 Screenshot 168 P2P OverflowVirtualCircuit ...
Page 420: ...Exinda Network Orchestrator 4 Settings 420 Screenshot 175 Students OverflowVirtualCircuit ...