Exinda Network Orchestrator
3 Using
|
338
NOTE
If there are appliances in the group or its sub-groups, then the group cannot be deleted.
If there is configuration on the group, but no appliances, it can be deleted.
3.
Confirm that you want delete the group.
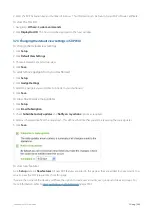
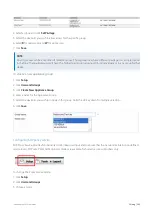
3.6.3 Configuration Library
The Configuration Library allows to you create items and save them for reuse in different areas, much like a template. For
instance, create a policy set once and then use it in multiple virtual circuits or in multiple Optimizer Policy Trees applied
to different appliance groups.
The library items will appear in drop-down lists when configuring other items. For example, when creating a policy, you
can select an application from a list; when creating a Optimizer Policy Tree, you can select a circuit from a list, or a virtual
circuit from a list, or a policy set from a list, and so on.
Library items are categorized as follows:
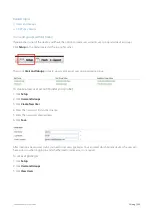
– Identifies the physical connections to the WAN or Internet by defining the inbound and outbound band-
width and the named circuit type. The circuits within a tenant must have unique names.
– An abstract concept used to identify the purpose of the circuit and appliance bridges and to create a
logical binding between the circuits and the appliance bridges.
– Logically divide or partition a circuit to define what traffic will be processed in this partition (and
when), and how much bandwidth it is allowed.
– Dynamic virtual circuits provide a means to configure fair sharing among the hosts, or to
configure a limit to the number of hosts so that those hosts get preferential treatment.
– Ordered list of policies that can be applied to one or more virtual circuits in one or more appliance
groups.
– Define the actions to perform on specific targeted traffic.
– Represent hosts on a network and can include subnets, single hosts, or groups of both. Once on
the appliance, network objects are used to determine if host and user traffic data are internal or external to the LAN
behind your appliance.
– Classify traffic by layer 7 signatures OR by a combination of network objects, ports, protocols, and
DSCP markings. You can then filter traffic generated by the applications to determine which policy to apply.
– Preset and custom groups of applications to monitor and subsequently classify traffic and
determine which policy to apply to traffic.
– Define a specific timeframe of the week. When used in policies or virtual circuits, the schedule will affect
traffic only within the identified timeframe.
Application Performance Scores
– Identify the applications operating on your network whose performance you
need to monitor.
– The Service Level Agreement (SLA) objects are used to monitor the availability of a par-
ticular IP site.
– Virtual LAN (VLAN) Objects are used to logically separate hosts (or groups of hosts) on a functional basis
rather than on a physical basis.
Summary of Contents for EXNV-10063
Page 369: ...Exinda Network Orchestrator 4 Settings 369 ...
Page 411: ...Exinda Network Orchestrator 4 Settings 411 Screenshot 168 P2P OverflowVirtualCircuit ...
Page 420: ...Exinda Network Orchestrator 4 Settings 420 Screenshot 175 Students OverflowVirtualCircuit ...