Exinda Network Orchestrator
4 Settings
|
482
certificate to sign other certificates is reasonable in situations where you want encryption but you do not need the third
party verification. The difference is that a warning is shown to the client for each server when using self-signed
certificates, whereas when using a self-signed CA certificate to sign multiple other certificates, the warning will only be
shown once for all the certificates that were signed by the CA certificate, that is, once the client trusts a certificate that is
signed by the self-signed CA certificate, the client automatically trusts all other certificates signed by that self-signed CA
certificate.
In the case where there are multiple virtual hosts on a single server, a Server Name Indication (SNI) is used to indicate
what virtual hostname the client is attempting to connect to during the handshaking process. This allows a single server
to present individual certificates for each of its multiple secure websites without requiring all of the sites to use the same
certificate.
How Exinda accelerates the SSL protocol
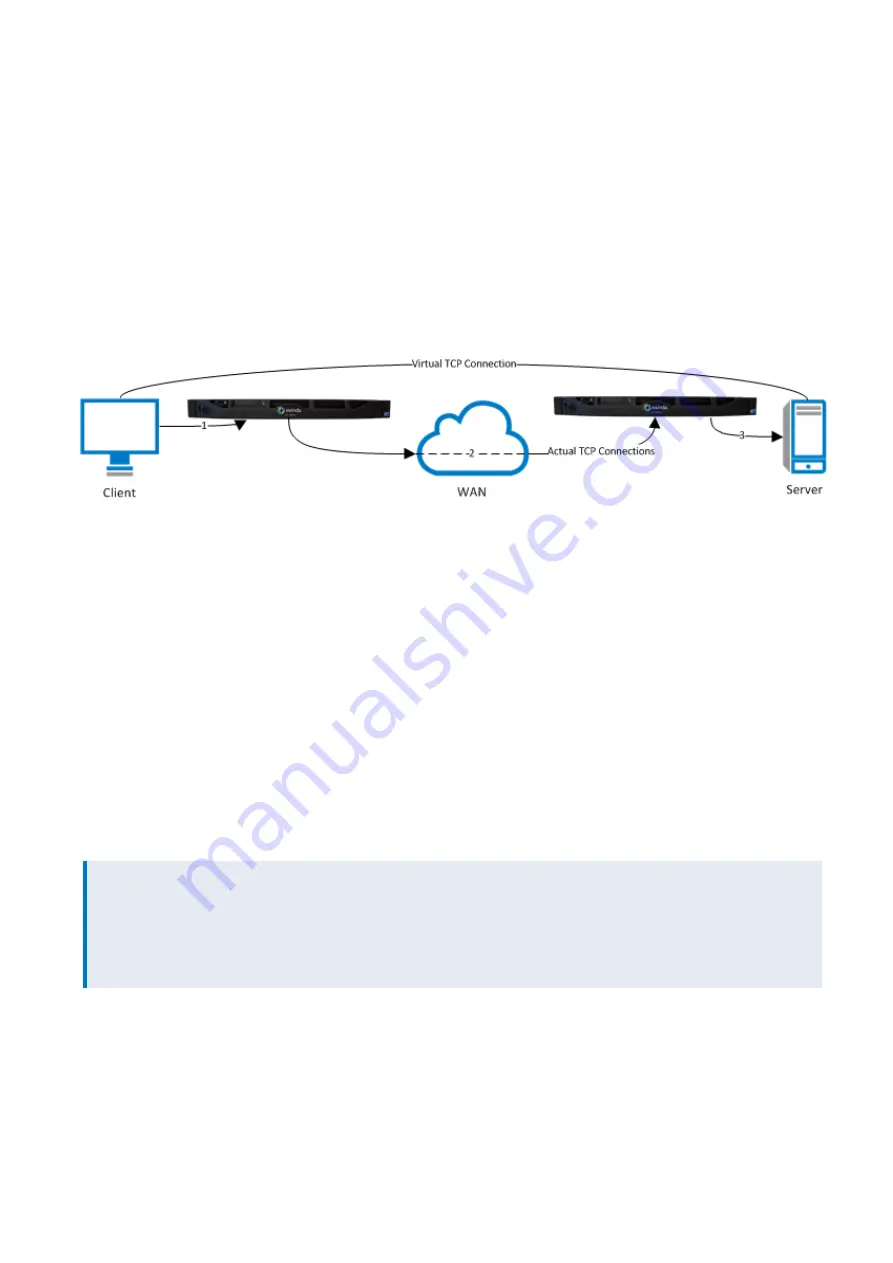
For SSL acceleration, a server-side Exinda appliance and a client-side appliance is put in line for this SSL traffic. The traffic
between these appliances are accelerated. The benefits that can be gained by generic application acceleration on
encrypted data are limited. For example, the Exinda WAN Memory technology achieves higher reduction on clear text
rather than encrypted data. However, the SSL acceleration feature is designed to overcome these limitations by
transparently decrypting accelerated traffic, performing the relevant application acceleration techniques such as TCP
Acceleration and WAN Memory, then re-encrypting the traffic again. This means Exinda can apply all application
acceleration technologies to the traffic as if it were clear text, while still maintaining SSL connections.
The server-side appliance will act on behalf of the client in the communication between the appliance and the server
and the client-side appliance will act on behalf of the server for communication between the client and the appliance.
In order to decrypt and re-encrypt the traffic, the Exinda appliances must have access to the appropriate certificate and
public key for each server that clients will communicate with over SSL. Furthermore, the Exinda appliances must be
configured to know which servers can receive traffic that is SSL accelerated. These servers are defined by IP address and
port, certificate, and other details. Only traffic to servers that are explicitly configured in this way is SSL accelerated. If the
server is hosting multiple virtual hosts, when defining the server, you can define an acceleration server for each of the
virtual hosts by specifying the SNI virtual host so that the virtual host name is presented during the handshake process
with the appliance.
NOTE
If you upload the appropriate certificates and configure SSL Acceleration Servers on the server-side appliance, the
appliance will use the Exinda acceleration community feature to push these certificates and server configurations to
the other appliances in the community. Configurations that have been pushed to the remote appliances will appear
in the
Remote SSL Acceleration Servers
list on the
Optimization > SSL
page.
By default, the Exinda appliances are pre-loaded with several root CA certificates. The site-specific certificates will be
loaded onto the appliances by the user (or distributed using the community feature). When the client attempts to access
the website, during the handshake, the appliance sends to the client all of the certificates in the chain of trust.
Summary of Contents for EXNV-10063
Page 369: ...Exinda Network Orchestrator 4 Settings 369 ...
Page 411: ...Exinda Network Orchestrator 4 Settings 411 Screenshot 168 P2P OverflowVirtualCircuit ...
Page 420: ...Exinda Network Orchestrator 4 Settings 420 Screenshot 175 Students OverflowVirtualCircuit ...
















































