Book Title
Ridgeline Concepts and Solutions Guide
312
XML files for third-party devices extend and further specify properties unique to each device type and
device. Extreme Networks devices are also recognized through this same ATL mechanism. When
Ridgeline discovers a device, it searches this hierarchy for a match to the device or device type that will
provide the properties for the device.
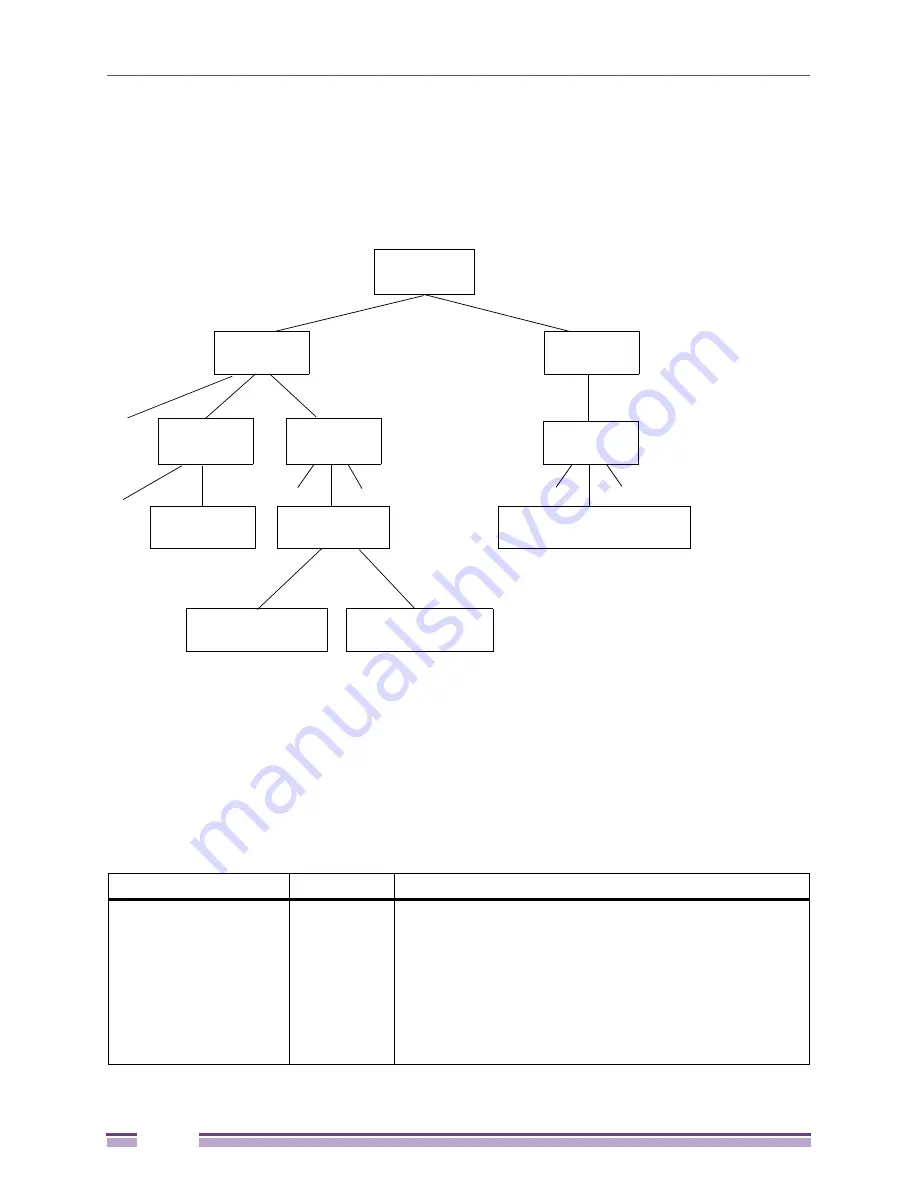
Figure 252: ATL XML file hierarchy
The 3COM SuperStacker II 1000 is an example of how a third-party device is integrated into Ridgeline
for Telnet functionality.
There are actually three 3COM devices integrated into Ridgeline, all of which share a number of
properties. Therefore, these properties are specified in the
3com.xml
file, which is referenced as the
parent in the
3Com_SuperstackerII_1100.xml
file.
The key attributes in an ATL XML file are the following:
Table 9: Attributes Used in an ATL File
TAG
Attribute
Value
Device Type
Name
The name of the device type of the device. This is the main Tag
in the file.
Version
Must be specified as “1”
Parent
The parent XML file. For an individual device model, this may be
the device type XML file (e.g. in the
3Com_SuperstackerII_1100.xml file, the parent is “3Com.xml”).
For a device type XML file, such as the 3COM.xml file, the
parent is “3rdParty.xml”.
Identity
Contains the sysObjectId tag
All Devices
3rd Party.xml
Extreme.xml
Extreme
Summit
Unmanaged
Extreme
Summit
_
48.xm
l
Summit
_
WM.xml
Summit
_
WM_100.xml
3Com.xml
3Com_SuperStackerII_1100.xml
Summit
_
WM_1000.xml
etc.
etc.
etc.
etc.
Summary of Contents for Ridgeline 3.0
Page 14: ...Related Publications Ridgeline Concepts and Solutions Guide 12 ...
Page 26: ...Ridgeline Overview Ridgeline Concepts and Solutions Guide 24 ...
Page 52: ...Getting Started with Ridgeline Ridgeline Concepts and Solutions Guide 50 ...
Page 78: ...Using Map Views Ridgeline Concepts and Solutions Guide 76 ...
Page 88: ...Provisioning Network Resources Ridgeline Concepts and Solutions Guide 86 ...
Page 103: ...6 Ridgeline Concepts and Solutions Guide 101 Figure 63 E Line Service Details Window ...
Page 104: ...Managing Ethernet Services Ridgeline Concepts and Solutions Guide 102 ...
Page 114: ...Importing Services Ridgeline Concepts and Solutions Guide 112 ...
Page 132: ...Managing and Monitoring VPLS Domains Ridgeline Concepts and Solutions Guide 130 ...
Page 146: ...Managing VLANs Ridgeline Concepts and Solutions Guide 144 ...
Page 190: ...Managing Your EAPS Configuration Ridgeline Concepts and Solutions Guide 188 ...
Page 202: ...Managing Network Security Ridgeline Concepts and Solutions Guide 200 ...
Page 350: ...Book Title Ridgeline Concepts and Solutions Guide 348 ...
Page 372: ...Book Title Ridgeline Concepts and Solutions Guide 370 ...