32
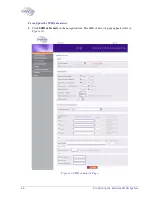
Configuring the Extricom WLAN System
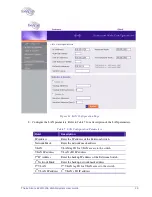
Table 9. Security Definition Parameters
Field
Description
Encryption & Authentication
Choose method
Define the method of encryption and authentication.
A combination of encryption and authentication methods may be
selected from the options detailed in the drop-down list.
Encryption cipher
There are three types of encryption ciphers available:
WEP64
– Wired Equivalent Privacy (802.11 encryption
protocol). This is a very basic encryption level. (AKA WEP40)
WEP128
– This encryption is similar to WEP64, but the WEP
keys are longer. (AKA WEP104)
TKIP
– Temporal Key Integrity Protocol. This is a more secure
and more advanced method of encryption as a part of the WPA
standard.
Authentication method
Authentication is used to identify if a wireless device is authorized
to connect to the WLAN, and verifies the wireless device’s
identity. Authentication methods (such as specific EAP methods
available in the
WPA
(Radius)
option) also verify that the
association process is secured. Authentication utilizing WPA
(Radius) can also support encryption key changes.
The following methods are available:
802.1x
– if the cipher is WEP or WEP104
WPA-PSK
or
WPA (Radius)
– if the cipher is TKIP
Supported protocols: EAP, TLS, TTLS, PEAP, LEAP and MD5
When choosing the encryption cipher and
authentication methods, you should take into
account your wireless devices’ capabilities.
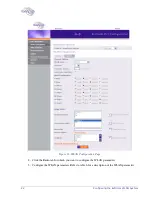
WEP Keys
The
WEP Keys
area is only enabled if the cipher selected in the
Choose Method
field is WEP or WEP104. In the WEP Keys area,
you define the WEP Key that is used for encrypting or decrypting.
You can define all four WEP keys. For each key you define, select
the input format (ASCII or HEX) and enter the key according to
the following table:
Cipher
ASCII
HEX
WEP64
(or WEP+802.1x)
5 characters
10 digits
WEP128
(or 802.1x)
13 characters
26 digits
Summary of Contents for EXSW-400
Page 1: ...Version 1 0 THE EXTRICOM WLAN SYSTEM WIRELESS OFFICE EDITION EXWO 404 USER GUIDE ...
Page 4: ......
Page 20: ......