34
Microsoft Exchange Server Roles
The product supports the following roles of Microsoft Exchange Server
2007:
Edge Server role
Hub Server role
Mailbox Server role
Combo Server (Mailbox Server and Hub Server roles)
Cluster Environment
The product supports the following cluster models of Microsoft Exchange
Server 2007:
Cluster Continuous Replication (CCR)
Single Copy Cluster (SCC)
For detailed instructions how to deploy and install the product on a
cluster, see “
Deploying the Product on a Cluster
.
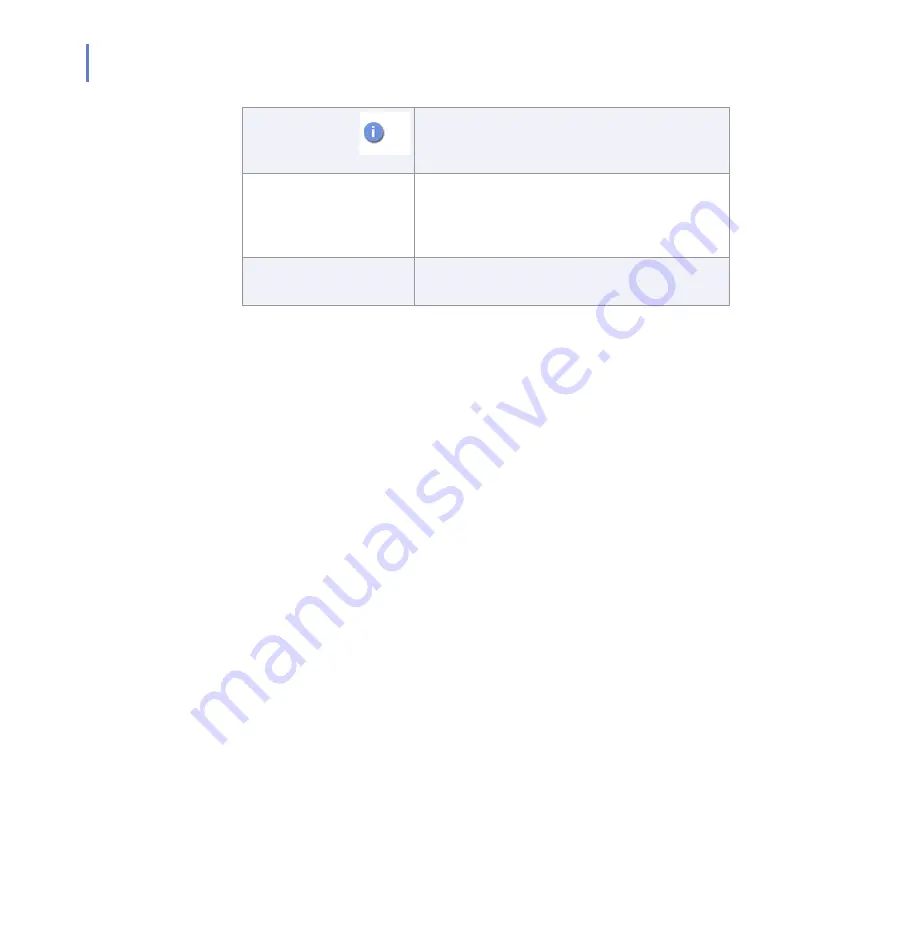
For performance and security reasons, it is
not possible to install the product on any other
than an NTFS partition.
Disk space for
processing:
10 GB or more. The required disk space
depends on the number of mailboxes, amount
of data traffic and the size of the Information
Store.
Other:
A CD-ROM drive is required if you are
installing the product from CD-ROM.
Summary of Contents for ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00
Page 1: ...F Secure Anti Virus for Microsoft Exchange Deployment Guide...
Page 6: ...4 ABOUT THIS GUIDE How This Guide Is Organized 5 Conventions Used in F Secure Guides 6...
Page 19: ...17 2 DEPLOYMENT Installation Modes 18 Network Requirements 19 Deployment Scenarios 20...
Page 64: ...62 4 CONFIGURING F SECURE SPAM CONTROL Overview 63 Realtime Blackhole List Configuration 64...
Page 106: ...104 B APPENDIX Services and Processes List of Services and Processes 105...
Page 115: ......