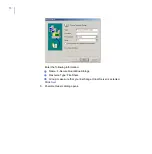
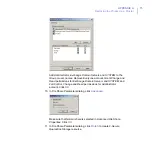
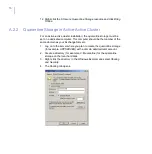
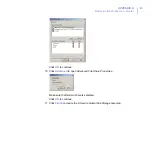
APPENDIX A
69
Deploying the Product on a Cluster
A.1
Installation Overview
Follow these steps to deploy and use F-Secure Anti-Virus for Microsoft
Exchange on a cluster.
1.
Install F-Secure Policy Manager on a dedicated server. If you already
have F-Secure Policy Manager installed in the network, you can use it
to administer F-Secure Anti-Virus for Microsoft Exchange. For more
information, see F-Secure Policy Manager Administrator’s Guide.
2.
Install Microsoft SQL Server 2000, 2005 or 2008 on a dedicated
server. Microsoft SQL Server must be installed with the mixed
authentication mode (Windows Authentication and SQL Server
Authentication). After the installation, make sure that
Named Pipes
and
TCP/IP protocols
are enabled in SQL Server network
configuration.
3.
Create the quarantine storage where the product will place
quarantined e-mail messages and attachments.
In the active-passive cluster environment, continue to “
Storage in Active-Passive Cluster
In the active-active cluster environment, continue to “
Storage in Active-Active Cluster
.
In the Single Copy Cluster (SCC) environment, continue to
“
Creating the Quarantine Storage for a Single Copy Cluster
In the Continuous Cluster Replication (CCR) environment,
continue to “
Creating the Quarantine Storage for a Continuous Cluster
.
In the Database Availability Group (DAG) environment continue
to “
Creating the Quarantine Storage for a Database Availability Group
Summary of Contents for ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00
Page 1: ...F Secure Anti Virus for Microsoft Exchange Deployment Guide...
Page 6: ...4 ABOUT THIS GUIDE How This Guide Is Organized 5 Conventions Used in F Secure Guides 6...
Page 19: ...17 2 DEPLOYMENT Installation Modes 18 Network Requirements 19 Deployment Scenarios 20...
Page 64: ...62 4 CONFIGURING F SECURE SPAM CONTROL Overview 63 Realtime Blackhole List Configuration 64...
Page 106: ...104 B APPENDIX Services and Processes List of Services and Processes 105...
Page 115: ......