APPENDIX A
87
Deploying the Product on a Cluster
4.
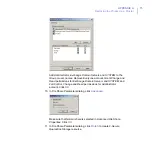
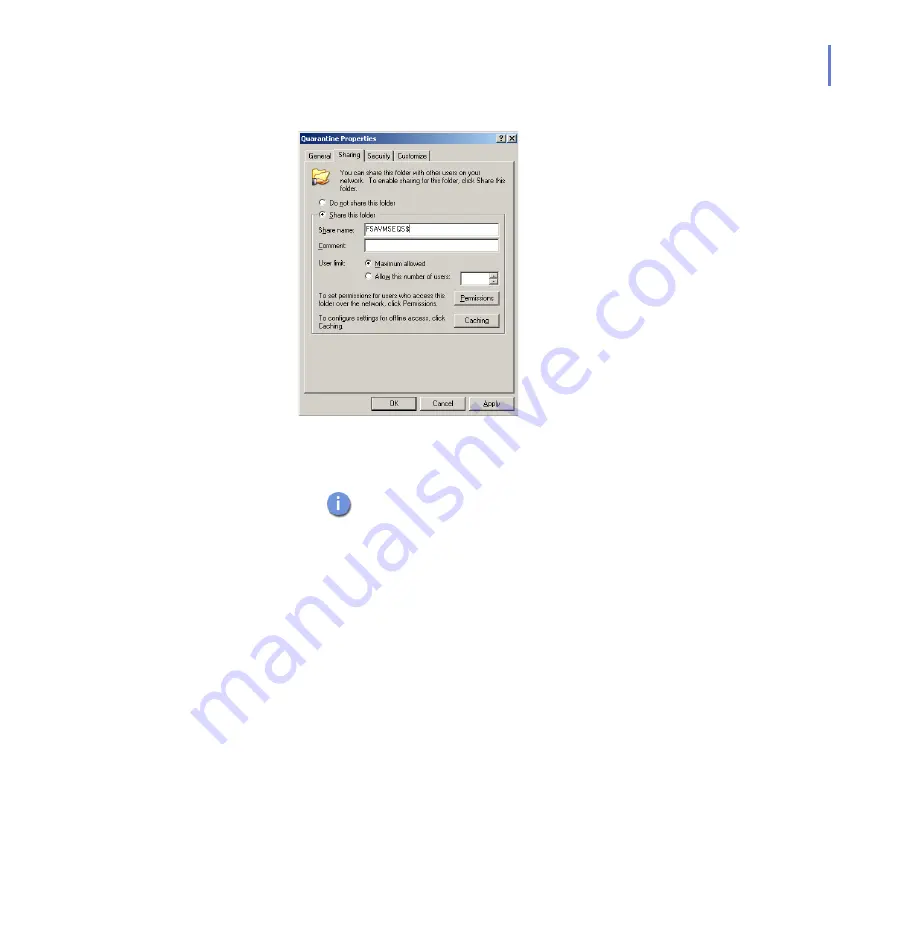
Go to the
Sharing
tab.
a.
Type
FSAVMSEQS$
as the share name and
F-Secure
Quarantine Storage
as comment.
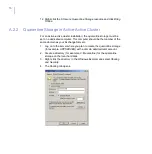
b.
Make sure that
User Limit
is set to
Maximum allowed
.
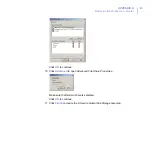
Click
Permissions
to set permissions.
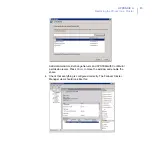
The dollar ($) character at the end of the share name
makes the share hidden when you view the network
resources of the cluster with Windows Explorer.
Summary of Contents for ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00
Page 1: ...F Secure Anti Virus for Microsoft Exchange Deployment Guide...
Page 6: ...4 ABOUT THIS GUIDE How This Guide Is Organized 5 Conventions Used in F Secure Guides 6...
Page 19: ...17 2 DEPLOYMENT Installation Modes 18 Network Requirements 19 Deployment Scenarios 20...
Page 64: ...62 4 CONFIGURING F SECURE SPAM CONTROL Overview 63 Realtime Blackhole List Configuration 64...
Page 106: ...104 B APPENDIX Services and Processes List of Services and Processes 105...
Page 115: ......