APPENDIX A
99
Deploying the Product on a Cluster
6.
Complete the installation on the first active node.
7.
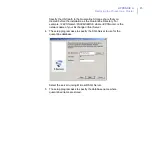
Log on to the second node of the cluster using a domain
administrator account and repeat steps 2-4.
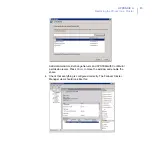
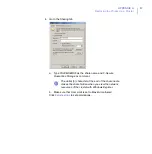
8.
After you specify the SQL Server to use, the setup wizard asks you to
specify the quarantine database.
Select
Use the existing database
.
9.
Complete the installation on the second node.
A.4
Administering the Cluster Installation with
F-Secure Policy Manager
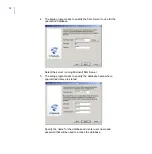
To administer the product installed on a cluster, create a new subdomain
under your organization or network domain. Import all cluster nodes to
this subdomain.
To change product configuration on all cluster nodes, follow these
instructions:
1.
Select the cluster subdomain in the Policy Domains tree.
2.
Change required settings.
Summary of Contents for ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00
Page 1: ...F Secure Anti Virus for Microsoft Exchange Deployment Guide...
Page 6: ...4 ABOUT THIS GUIDE How This Guide Is Organized 5 Conventions Used in F Secure Guides 6...
Page 19: ...17 2 DEPLOYMENT Installation Modes 18 Network Requirements 19 Deployment Scenarios 20...
Page 64: ...62 4 CONFIGURING F SECURE SPAM CONTROL Overview 63 Realtime Blackhole List Configuration 64...
Page 106: ...104 B APPENDIX Services and Processes List of Services and Processes 105...
Page 115: ......