CHAPTER 7
219
Administering F-Secure Content Scanner Server
There is a security risk associated with
password protected archives because their
content cannot be inspected without a password
that is known only to the sender and (in most of
the cases) the recipient.
If the recipients do not have any virus protection
on their workstations, or if the virus protection is
not up-to-date, malicious code in a password
protected archive can get through.
Password protected archives are not detected if
scanning inside archives is disabled.
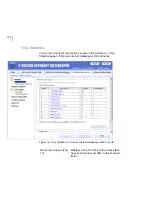
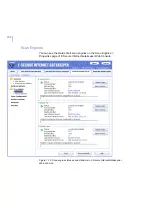
Acceptable unpacked
size threshold
Specify the acceptable unpacked size (in
kilobytes) for archive files. If the unpacked size
of an archive file exceeds this threshold, the
server will consider the archive suspicious and
corresponding action will be taken.
Scan extensions
inside archives
Specify a list of files, separated by spaces, that
are scanned inside archives.
You can also use wildcards (*, ?). To scan all
files, use '*'. To specify files with no extension,
type a dot ('.').
Example: "EXE COM DO? *HTM".
Extensions allowed in
password protected
archives
Specify a list of file extensions, separated by
spaces, that are allowed in password protected
archives.
You can also use wildcards: '?' matches exactly
one character, '*' matches any number of
characters, including zero (0) characters.
For example: "DO? *ML".
File extensions are used for recognizing the file
types in password protected archives.
Max scan timeout
Specify how long a scan task can be carried out
before it is automatically cancelled.
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...