APPENDIX F
333
Advanced Deployment Options
F.3.3
Load Balancing with Proxy or Firewall
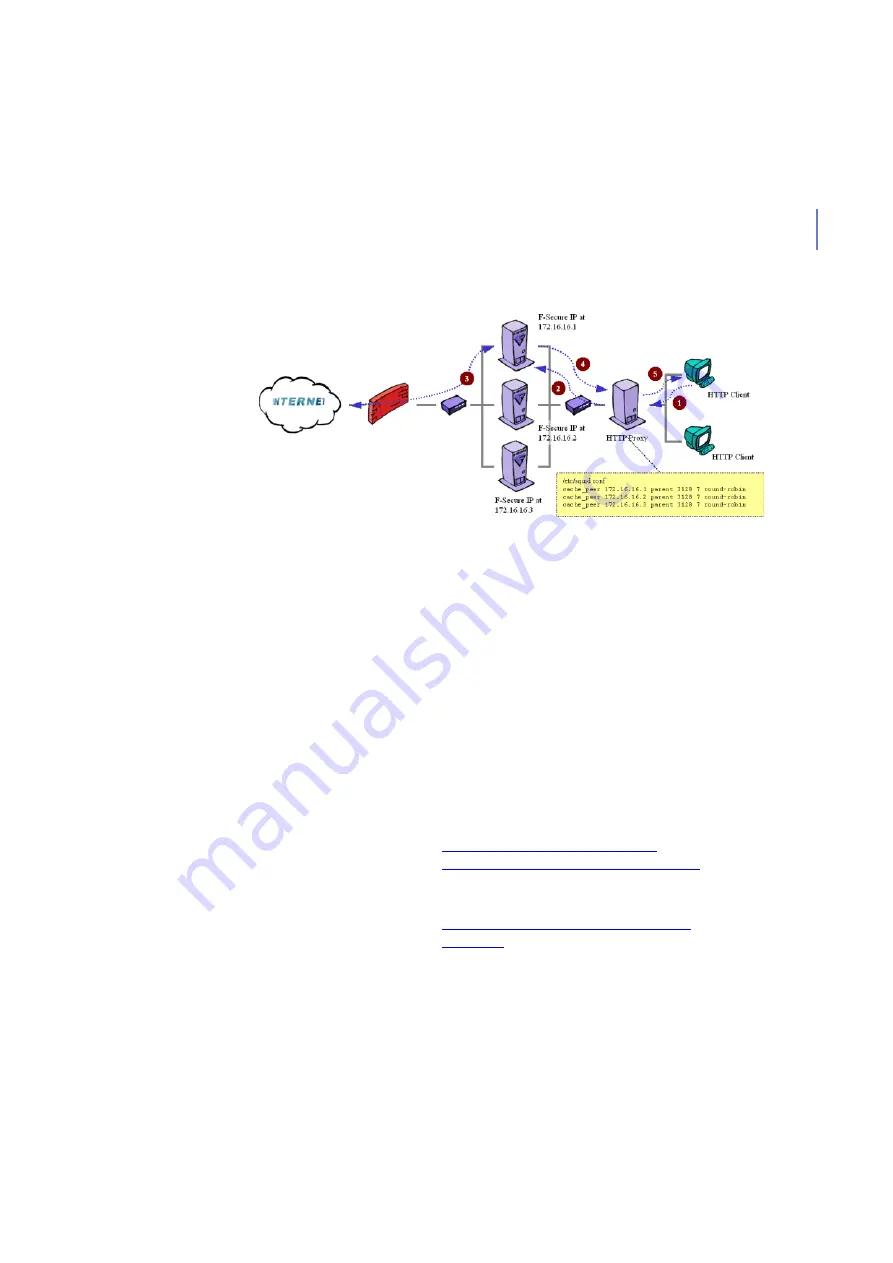
Figure F-4 F-Secure Anti-Virus for Internet Gateways deployed with HTTP proxy
Clients have to configure web browsers to use a HTTP proxy. If
the upstream proxy is transparent, clients do not require any
configuration. Using round-robin or some other load-sharing
model, the upstream proxy redirects requests to proxy peers
specified in its configuration file.
Benefits
Fairly easy to implement.
If a company already has a proxy server, clients do not need to be
configured in any way.
Squid
Load balancing can be achieved with
cache_peer options. See example
configuration here:
http://www.squid-cache.org/Doc/
Hierarchy-Tutorial/tutorial-7.html#ss7.3
SQUID Frequently Asked Questions:
Summary of Contents for INTERNET GATEKEEPER WINDOWS 2000-2003 SERVER 6.61...
Page 1: ...F Secure Internet Gatekeeper Windows 2000 2003 Server Administrator s Guide...
Page 10: ...10 ABOUT THIS GUIDE How This Guide is Organized 11 Conventions Used in F Secure Guides 13...
Page 26: ...26 2 DEPLOYMENT Overview 27 Deployment Scenarios 29...
Page 58: ...58 Step 10 Enter the IP address of the F Secure Policy Manager Server Click Next to continue...
Page 261: ...CHAPTER10 261 Quarantine Management Figure 10 1 Quarantine Query page...
Page 296: ...296 A APPENDIX Warning Messages HTTP Warning Messages 297 SMTP Warning Messages 298...
Page 304: ...304 C APPENDIX Access Log Variables List of Access Log Variables 305...
Page 309: ...309 D APPENDIX Mail Log Variables List of Mail Log Variables 310...
Page 360: ...360 G APPENDIX Services and Processes List of Services and Processes 361...
Page 414: ...414...